Page011
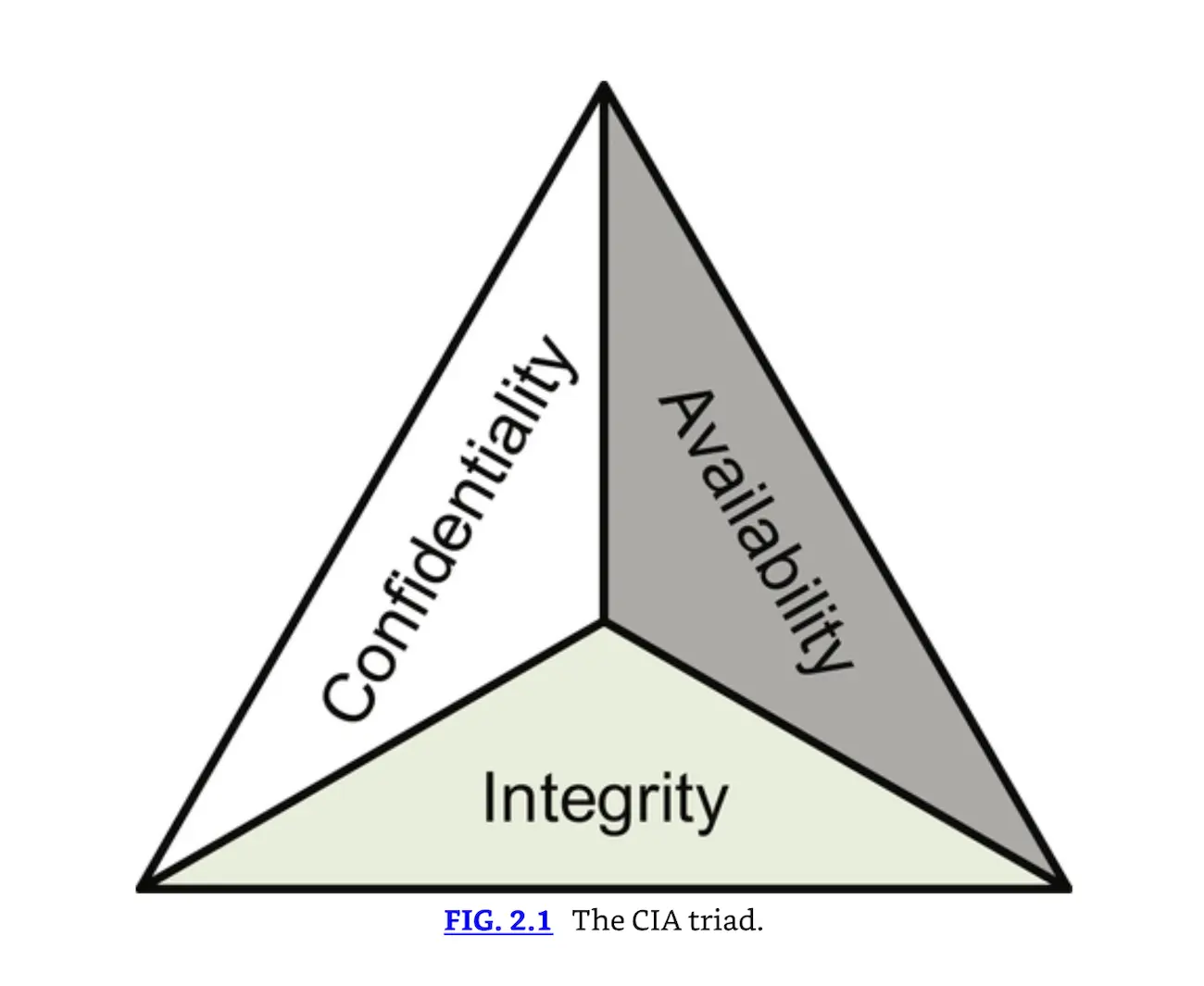 The CIA triad.
The CIA triad.
All three pieces of the CIA triad work together to provide assurance that data and systems remain secure. Do not assume that one part of the triad is more important than another. Every IT system will require a different prioritization of the three, depending on the data, user community, and timeliness required for accessing the data. There are opposing forces to CIA. As shown in Fig. 2.2, those forces are disclosure, alteration, and destruction (DAD).
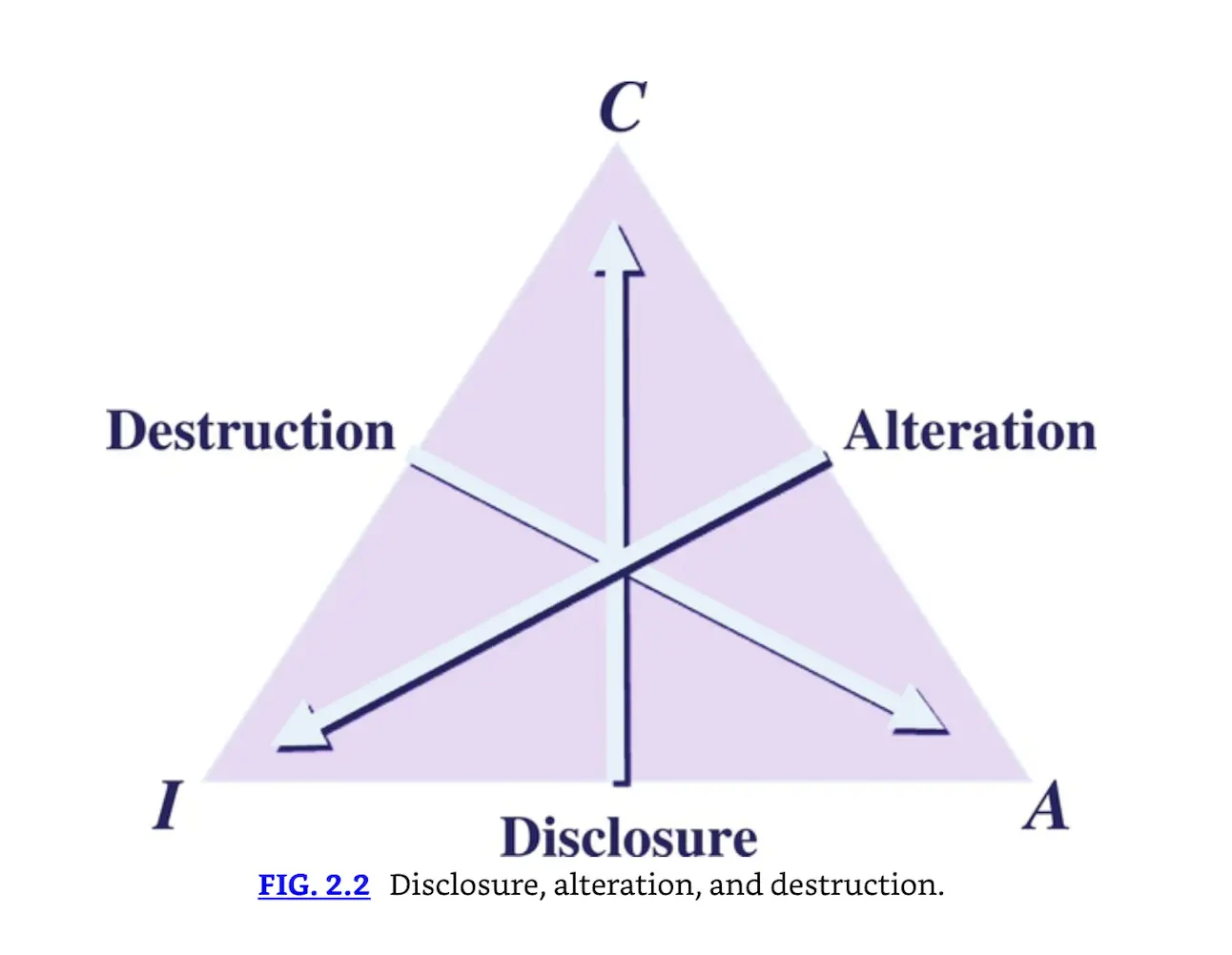 Disclosure, alteration, and destruction.
Disclosure, alteration, and destruction.
Confidentiality
Confidentiality seeks to prevent the unauthorized disclosure of information: it keeps data secret. In other words, confidentiality seeks to prevent unauthorized read access to data. An example of a confidentiality attack would be the theft of Personally Identifiable Information (PII), such as credit card information.
Data must only be accessible to users who have the clearance, formal access approval, and the need to know. Many nations share the desire to keep their national security information secret and accomplish this by ensuring that confidentiality controls are in place.