Page013
Identity and Authentication, Authorization, and Accountability (AAA)
The term “AAA” is often used to describe the cornerstone concepts Authentication, Authorization, and Accountability. Left out of the AAA acronym is Identification (which is required, before the remaining three “A’s” can be achieved).
Identity and Authentication
Identity is a claim: if your name is “Person X,” you identify yourself by saying, “I am Person X.” Identity alone is weak because there is no proof. You can also identify yourself by saying, “I am Person Y.” Proving an identity claim is called authentication: you authenticate the identity claim, usually by supplying a piece of information or an object that only you possess, such as a password in the digital world, or your passport in the physical world.
When you check in at the airport, the ticket agent asks for your name (your identity). You can say anything you would like, but if you lie you will quickly face a problem: the agent will ask for your driver’s license or passport. In other words, they will seek to authenticate your identity claim.
Fig. 2.4 shows the relationship between identity and authentication. User Deckard logs into his email account at ericconrad.com. He types “deckard” in the username box; this is his identity on the system. Note that Deckard could type anything in the username box: identification alone is weak. It requires proof, which is authentication. Deckard then types a password, “R3plicant!” This is the correct password for the user Deckard at ericconrad.com, so Deckard’s identity claim is proven and he is logged in.
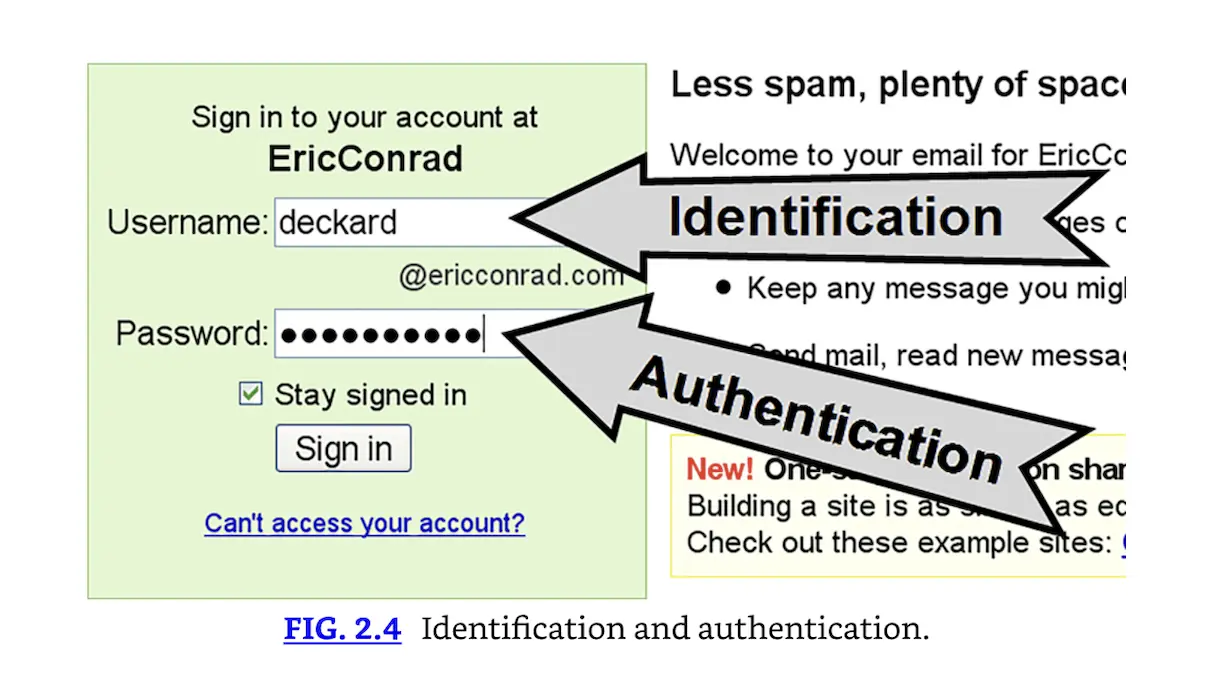 Identification and authentication.
Identification and authentication.
Identities must be unique: if two employees are named John Smith, their usernames (identities) cannot both be jsmith: this would harm accountability. Sharing accounts (identities) also harms accountability: policy should forbid sharing accounts, and security awareness should be conducted to educate users of this risk.
Ideally, usernames should be non-descriptive. The example username “jsmith” is a descriptive username: an attacker could guess the username by simply knowing the user’s actual name. This would provide one half (a valid identity) of the information required to launch a successful password-guessing attack (the second half is jsmith’s password, required to authenticate). A non-descriptive identity of “bcon1203” would make password-guessing attacks (and many other types of attacks) more difficult.
Authorization
Authorization describes the actions you can perform on a system once you have been identified and authenticated. Actions may include reading, writing, or executing files or programs. If you are an information security manager for a company with a human resources database, you may be authorized to view your own data and perhaps some of your employees’ data (such as accrued sick time or vacation time). You would not be authorized to view the CIO’s salary.