Page058
Hacktivist
A hacktivist is a hacker activist, someone who attacks computer systems for political reasons. “Hacktivism” is hacking activism. Many cases of hacktivism erupted surrounding the Russian invasion of Ukraine in 2022. Hacktivists supportive of both Ukraine as well as actors supportive of Russia engaged in substantial and widespread operations[^20]. A noteworthy aspect in these hacktivism campaigns includes Ukrainian Vice Prime Minister Mykhailo Fedorov's overt call on Twitter for individuals to join the "IT army" and attack specific Russian organizations and websites[^21].
Bots and Botnets
A “bot” (short for robot) is a computer system running malware that is controlled via a botnet. A botnet contains a central command and control (C&C) network, managed by humans called bot herders. The term “zombie” is sometimes used to describe a bot.
Many botnets used Internet Relay Chat (IRC) networks to provide command and control; modern botnets more commonly use HTTP, HTTPS, DNS, or proprietary protocols (sometimes obscured or encrypted).
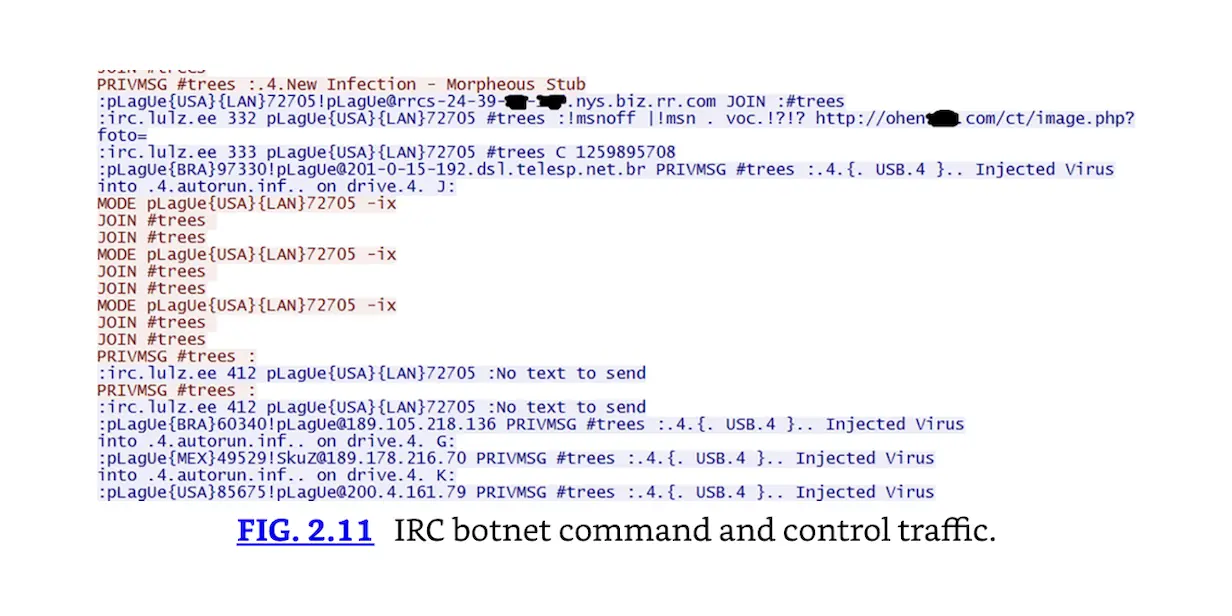 IRC botnet command and control traffic.
IRC botnet command and control traffic.
The bot in Fig. 2.11 (called pLagUe{USA}{LAN}72705, indicating it is in the United States) reports to the C&C network. Other bots report in from Brazil (BRA), Mexico (MEX), and the United States. They report injecting viruses into autorun.inf: they are most likely infecting attached USB drives with viruses.
Systems become bots after becoming compromised via a variety of mechanisms, including server-side attacks, client-side attacks, and running Remote Access Trojans (RATs). As described in Domain 3: Security Architecture and Engineering, a Trojan horse program performs two functions, one overt (such as playing a game) and one covert (such as joining the system to a botnet).
Once joined to a botnet, the bot may be instructed to steal local information such as credit card numbers or credentials for other systems, including online banks. Bots also send spam, host illicit websites including those used by drug-sale spam, and are used in coordinated Distributed Denial of Service (DDoS) attacks.