Page088
Zero Trust
Zero Trust (also called Zero Trust Architecture, or ZTA) is a reaction to classic perimeter firewall design. That (dated) model used a castle wall metaphor: outside the firewall was untrusted, and inside (behind the firewall) was trusted. Dual-factor authentication and encryption were commonly used for remote access, but not internal (since the inside was trusted). This design led to flat networks with little or no filtering for internal networks. The problem with this design is that most networks suffer intrusions at some point, and malware and malicious actors can spread far more quickly on trusted flat networks.
There are three core Zero Trust concepts:
- Ensure that all Resources are Accessed Securely Regardless of Location
- Adopt a Least Privilege Strategy and Strictly Enforce Access Control
- Concept #3—Inspect and Log All Traffic [7]
Zero Trust can be summarized as “Never Trust, Always Verify” [5]. Every device is considered untrusted, whether local or remote. All traffic to/from every system must be filtered (this is called micro-segmentation). All network traffic must be encrypted. Multi-factor authentication must be used in all cases. Fig. 4.1 shows a NIST diagram that illustrates the difference between classic perimeter design and zero trust.
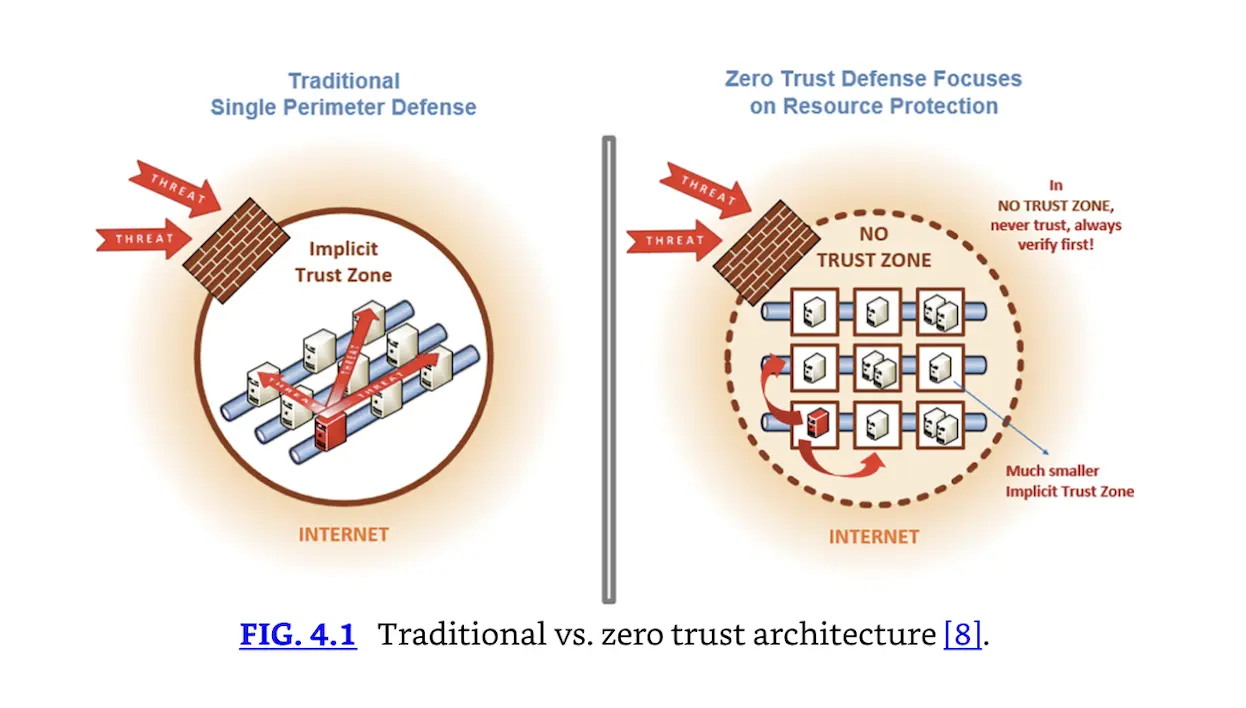
Forrester analyst John Kindervag formalized the concept of zero trust in 2009:
I created the concept of zero trust, which is framed around the principle that no network user, packet, interface, or device—whether internal or external to the network—should be trusted. Some people mistakenly think zero trust is about making a system trusted, but it really involves eliminating the concept of trust from cybersecurity strategy. By doing this, every user, packet, network interface, and device is granted the same default trust level: zero [9].
Technologies such as Software Defined Networking (SDN, discussed in Chapter 5, Domain 4: Communication and Network Security) can be used to achieve zero trust.