Page089
Security Models
Security models provide “rules of the road” for securely operating systems. The canonical example is Bell-LaPadula, which includes “No Read Up” (NRU), also known as the Simple Security Property. This is the rule that forbids a secret-cleared subject from reading a top secret object. While Bell-LaPadula is focused on protecting confidentiality, other models, such as Biba, are focused on integrity.
Reading Down and Writing Up
The concepts of reading down and writing up apply to Mandatory Access Control models such as Bell-LaPadula. Reading down occurs when a subject reads an object at a lower sensitivity level, such as a top secret subject reading a secret object. Fig. 4.2 shows this action.
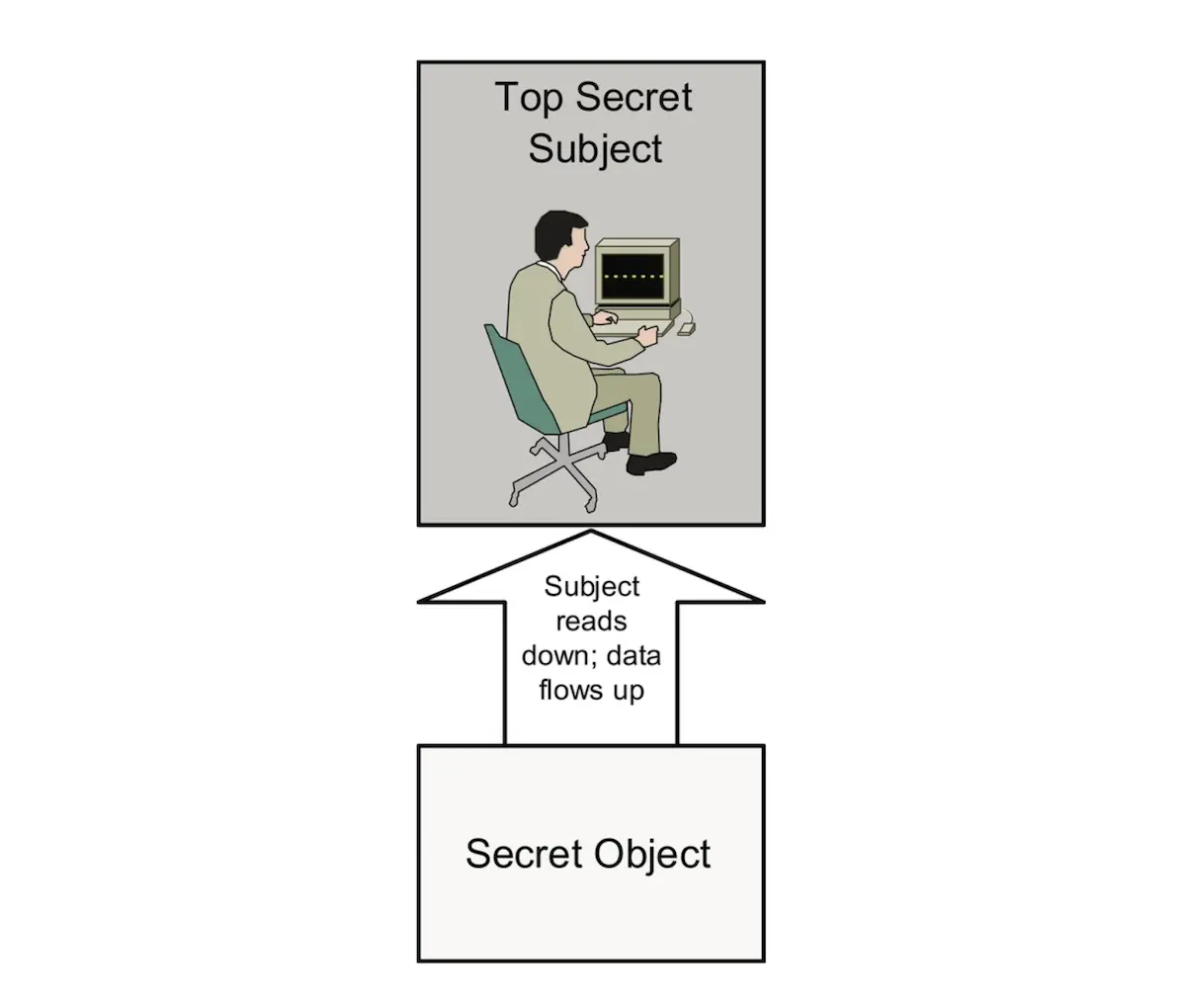
There are instances when a subject has information and passes that information up to an object, which has higher sensitivity than the subject has permission to access. This is called “writing up” because the subject does not see any other information contained within the object.
Writing up may seem counterintuitive. As we will see shortly, these rules protect confidentiality, often at the expense of integrity. Imagine a secret-cleared agent in the field uncovers a terrorist plot. The agent writes a report, which contains information that risks exceptionally grave damage to national security. The agent therefore labels the report top secret (writes up). Fig. 4.3 shows this action. The only difference between reading up and writing down is the direction that information is being passed. It is a subtle but important distinction for the CISSP® exam.