Page095
Access Control Matrix
An access control matrix is a table that defines access permissions between specific subjects and objects. A matrix is a data structure that acts as a table lookup for the operating system. For example, Table 4.1 is a matrix that has specific access permissions defined by user and details what actions they can enact. User rdeckard has read/write access to the data file as well as access to the data creation application. User etyrell can read the data file and still has access to the application. User rbatty has no access within this data access matrix.
Table 4.1 User Access Permissions
| Users | Data Access File # 1 | Data Creation Application |
|---|---|---|
| rdeckard | Read/Write | Execute |
| etyrell | Read | Execute |
| rbatty | None | None |
Zachman Framework for Enterprise Architecture
The Zachman Framework for Enterprise Architecture provides six frameworks for providing information security, asking what, how, where, who, when, and why, and mapping those frameworks across roles including planner, owner, designer, builder, programmer, and user. These frameworks and roles are mapped to a matrix, as shown in Fig. 4.6.
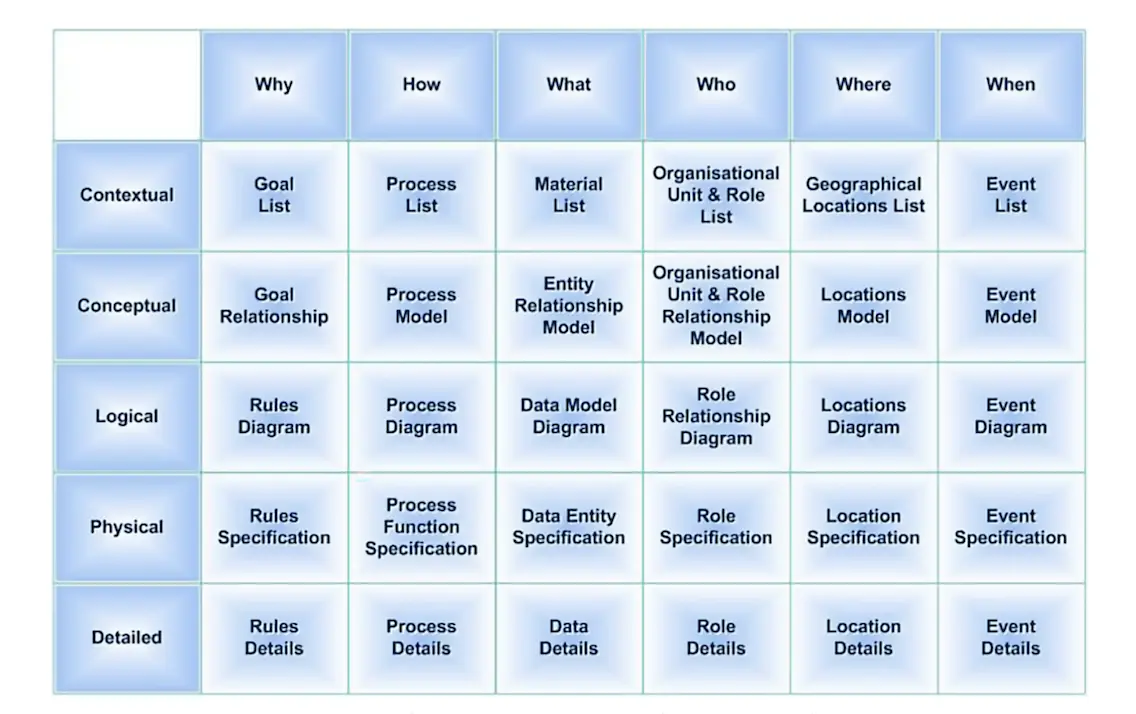 Zachman Framework. Source: https://commons.wikimedia.org/wiki/File:The_Zachman_Framework_of_Enterprise_Architecture.jpg; Image by: Ideasintegration, text by: SunSw0rd(text)/Wikimedia Commons. Image under permission of Creative Commons Attribution-Share Alike 3.0 Unported.
Zachman Framework. Source: https://commons.wikimedia.org/wiki/File:The_Zachman_Framework_of_Enterprise_Architecture.jpg; Image by: Ideasintegration, text by: SunSw0rd(text)/Wikimedia Commons. Image under permission of Creative Commons Attribution-Share Alike 3.0 Unported.
Graham-Denning Model
The Graham-Denning Model has three parts: objects, subjects, and rules. It provides a more granular approach to interaction between subjects and objects. There are eight rules:
- R1: Transfer Access
- R2: Grant Access
- R3: Delete Access
- R4: Read Object
- R5: Create Object
- R6: Destroy Object
- R7: Create Subject
- R8: Destroy Subject [12]
Harrison-Ruzzo-Ullman Model
The Harrison-Ruzzo-Ullman (HRU) Model maps subjects, objects, and access rights to an access matrix. It is considered a variation of the Graham-Denning Model. HRU has six primitive operations:
- Create object
- Create subject
- Destroy subject
- Destroy object
- Enter right into access matrix
- Delete right from access matrix [13]
In addition to HRU’s different operations, it differs from Graham-Denning because it considers subjects to be also objects.