Page110
Private clouds house data for a single organization, and may be operated by a third party, or by the organization itself. Government clouds are designed to keep data and resources geographically contained within the borders of one country, designed for the government of the respective country.
Benefits of cloud computing include reduced upfront capital expenditure, reduced maintenance costs, robust levels of service, and overall operational cost-savings.
From a security perspective, taking advantage of public cloud computing services requires strict service level agreements and an understanding of new sources of risk. One concern is multiple organizations’ guests running on the same host. The compromise of one cloud customer could lead to compromise of other customers.
Also, many cloud providers offer pre-configured system images, which may introduce risks via insecure configuration. For example, imagine a blog service image, with the operating system, Web service, and blogging software all pre-configured. Any vulnerability associated with the pre-configured image can introduce risk to every organization that uses the image.
Learn by Example
Pre-owned Images
In 2011 Amazon sent email to some EC2 (Elastic Cloud Compute) customers, warning them that “It has recently come to our attention that a public AMI in the US-East region was distributed with an included SSH public key that will allow the publisher to log in as root” [16].
AMI stands for Amazon Machine Image, a pre-configured virtual guest. TippingPoint’s DVLabs described what happened: “The infected image is comprised of Ubuntu 10.4 server, running Apache and MySQL along with PHP … the image appears to have been published … 6 months ago and we are only hearing about this problem now. So what exactly happened here? An EC2 user that goes by the name of guru created this image, with the software stack he uses most often and then published it to the Amazon AMI community. This would all be fine and dandy if it wasn’t for one simple fact. The image was published with his SSH key still on it. This means that the image publisher, in this case guru, could log into any server instance running his image as the root user. The keys were left in
/root/.ssh/authorized_keysand/home/ubuntu/.ssh/authorized_keys. We refer to the resulting image as ‘certified pre-owned’. The publisher claims this was purely an accident, a mere result of his inexperience. While this may or may not be true, this incident exposes a major security hole within the EC2 community” [16].
Organizations must analyze the risk associated with pre-configured cloud-based systems and consider the option of configuring the system from the “ground up,” beginning with the base operating system.
Organizations should also negotiate specific rights before signing a contract with a cloud computing provider. These rights include the right to audit, the right to conduct a vulnerability assessment, and the right to conduct a penetration test (both electronic and physical) of data and systems placed in the cloud.
Finally, do you know where your data is? Public clouds may potentially move data to any country, potentially beyond the jurisdiction of the organization’s home country. For example: US-based laws such as HIPAA (Health Insurance Portability and Accountability Act) or GLBA (Gramm-Leach-Bliley Act) have no effect outside of the United States. Private or government clouds should be considered in these cases.
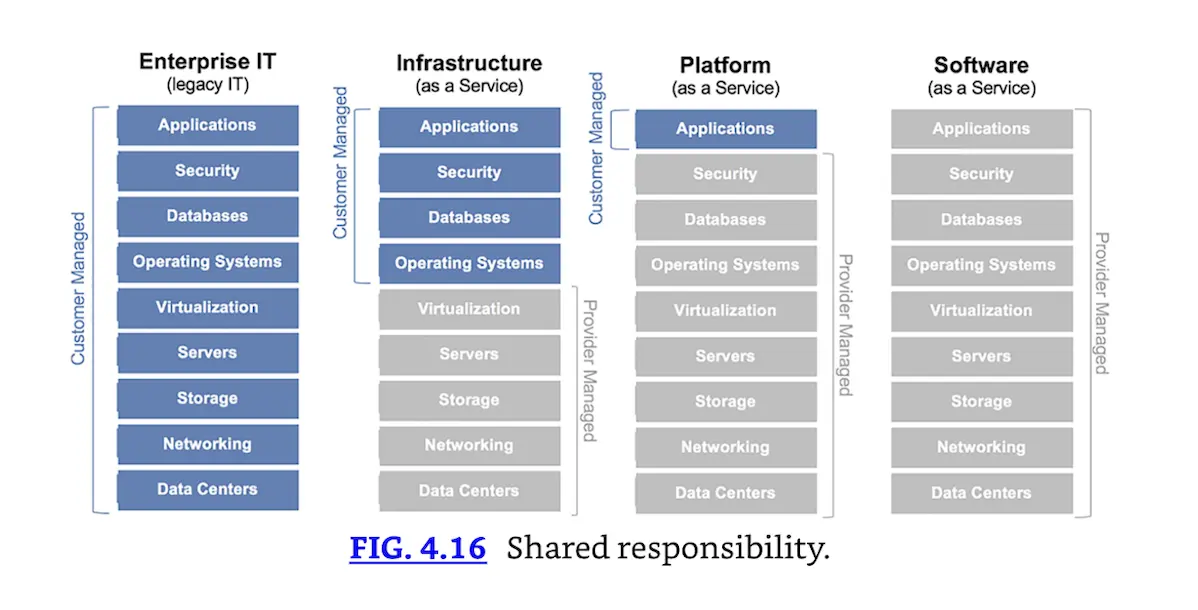
Shared Responsibility
Responsibility in the pre-cloud world was simpler. As we will discuss shortly, the demarc (line of demarcation) describes the respective responsibilities of the customer (their router and everything behind it) and the ISP (the ISP’s router and everything behind that). The shared responsibility is literally one cable connecting those two routers. “Responsibility” describes who is responsible for configuring, maintaining, and securing the systems on either side of the demarc. It also reflects both responsibility for availability (uptime) and legal responsibility.
By its nature, responsibility is more complex in the cloud. FIG. 4.16 from the General Services Administration (GSA), is a great graphic [17] describing the range of responsibilities from on-premises (labeled enterprise IT, where the customer is 100% responsible) to IaaS, PaaS, and SaaS (where the cloud provider has the most responsibility).