Page132
MixColumns
MixColumns also provides diffusion by “mixing” the columns of the State via finite field mathematics, as shown in Table 4.10.
Table 4.10 MixColumns.
SubBytes
The SubBytes function provides confusion by substituting the bytes of the State. The bytes are substituted according to a substitution table (also called an S-Box).
To use the table, take the byte of the State to be substituted (assume the byte is the letter “T”). ASCII “T” is hexadecimal byte “53.” Look up 5 on the X row and 3 on the Y column, resulting in hexadecimal byte “ed”; this replaces “53” in the State. Fig. 4.24 shows the AES substitution table directly from FIPS-197, with the byte 53 lookup overlaid on top.
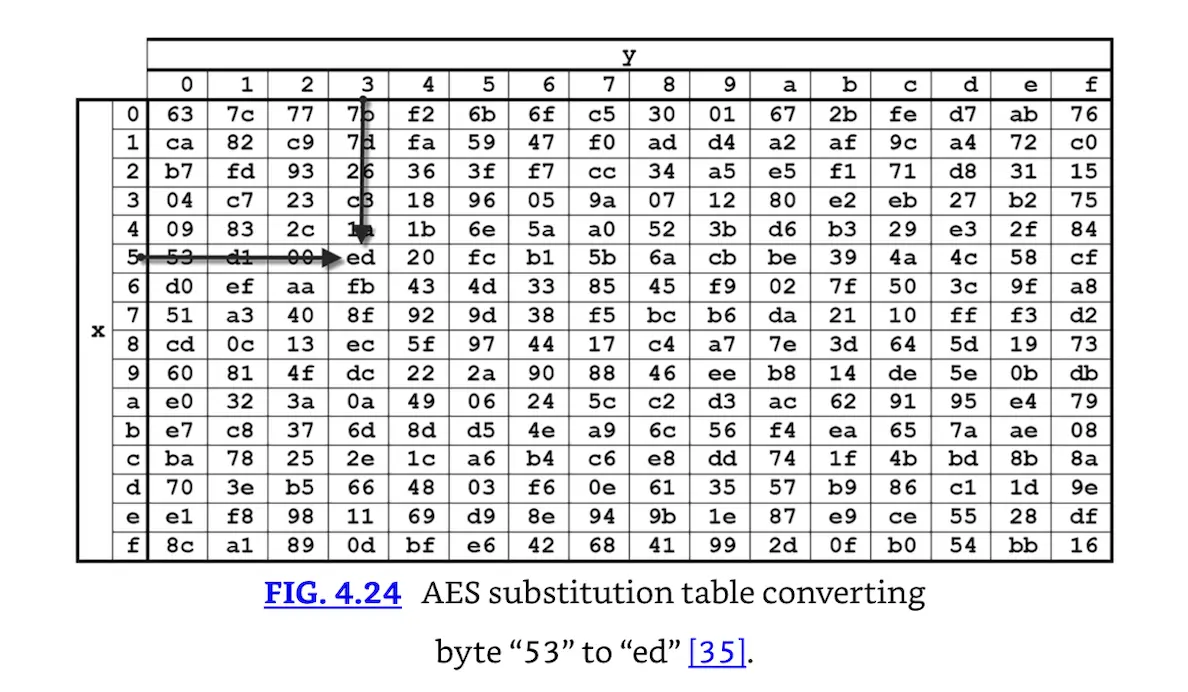 AES substitution table converting byte “53” to “ed” [35].
AES substitution table converting byte “53” to “ed” [35].
AddRoundKey
AddRoundKey is the final function applied in each round. It XORs the State with the subkey. The subkey is derived from the key and is different for each round of AES.
Blowfish and Twofish
Blowfish and Twofish are symmetric block ciphers created by teams led by Bruce Schneier, author of Applied Cryptography. Blowfish uses from 32- through 448-bit (the default is 128) keys to encrypt 64 bits of data. Twofish was an AES finalist, encrypting 128-bit blocks using 128- through 256-bit keys. Both are open algorithms, unpatented and freely available.
RC5 and RC6
RC5 and RC6 are symmetric block ciphers developed by RSA Laboratories. RC5 uses 32- (testing purposes), 64- (replacement for DES), or 128-bit blocks. The key size ranges from zero to 2040 bits.
RC6 was an AES finalist. It is based on RC5, altered to meet the AES requirements. It is also stronger than RC5, encrypting 128-bit blocks using 128-, 192-, or 256-bit keys.