Page136
Cryptographic Attacks
Cryptographic attacks are used by cryptanalysts to recover the plaintext without the key. Please remember that recovering the key (sometimes called “steal the key”) is usually easier than breaking modern encryption. This is what law enforcement typically does when faced with a suspect using cryptography: they obtain a search warrant and attempt to recover the key.
Brute Force
A brute-force attack generates the entire key space, which is every possible key. Given enough time, the plaintext will be recovered. This is an effective attack against all key-based ciphers, except for the one-time pad. Since the key of a one-time pad is the same length as the plaintext, brute forcing every possible key will eventually recover the plaintext, but it will also produce vast quantities of other potential plaintexts, including all the works of Shakespeare. A cryptanalyst would have no way of knowing which potential plaintext is real. This is why the one-time pad is the only provably unbreakable form of crypto.
Social Engineering
Social engineering uses the human mind to bypass security controls. This technique may be used to recover a key by tricking the key holder into revealing the key. Techniques are varied and include impersonating an authorized user when calling a help desk, and requesting a password reset. Information Security Europe tried a more direct route by asking users for their password in exchange for a treat: “More than one in five London office workers who talked to a stranger outside a busy train station were willing to trade a password for a chocolate bar” [39].
Rainbow Tables
A Rainbow Table is a pre-computed compilation of plaintexts and matching ciphertexts (typically passwords and their matching hashes). Rainbow tables greatly speed up many types of password cracking attacks, often taking minutes to crack where other methods (such as dictionary, hybrid, and brute-force password cracking attempts) may take much longer. We will discuss these methods of password cracking in Chapter 6, Domain 5: Identity and Access Management.
Many believe that rainbow tables are simply large databases of password/hash combinations. While this is how they appear to work (albeit at a typical speed of minutes and not seconds or less per lookup), this is not how rainbow tables work internally.
While pre-computation has obvious advantages, terabytes (or much more) would be required to store that much data using a typical database. All possible Microsoft LANMAN hashes and passwords would take roughly 48 terabytes of data to store; yet the Ophcrack rainbow table Linux live distribution (shown in Fig. 4.25) can crack 99% of LANMAN hashes using only 388 megabytes for table storage. How is this possible?
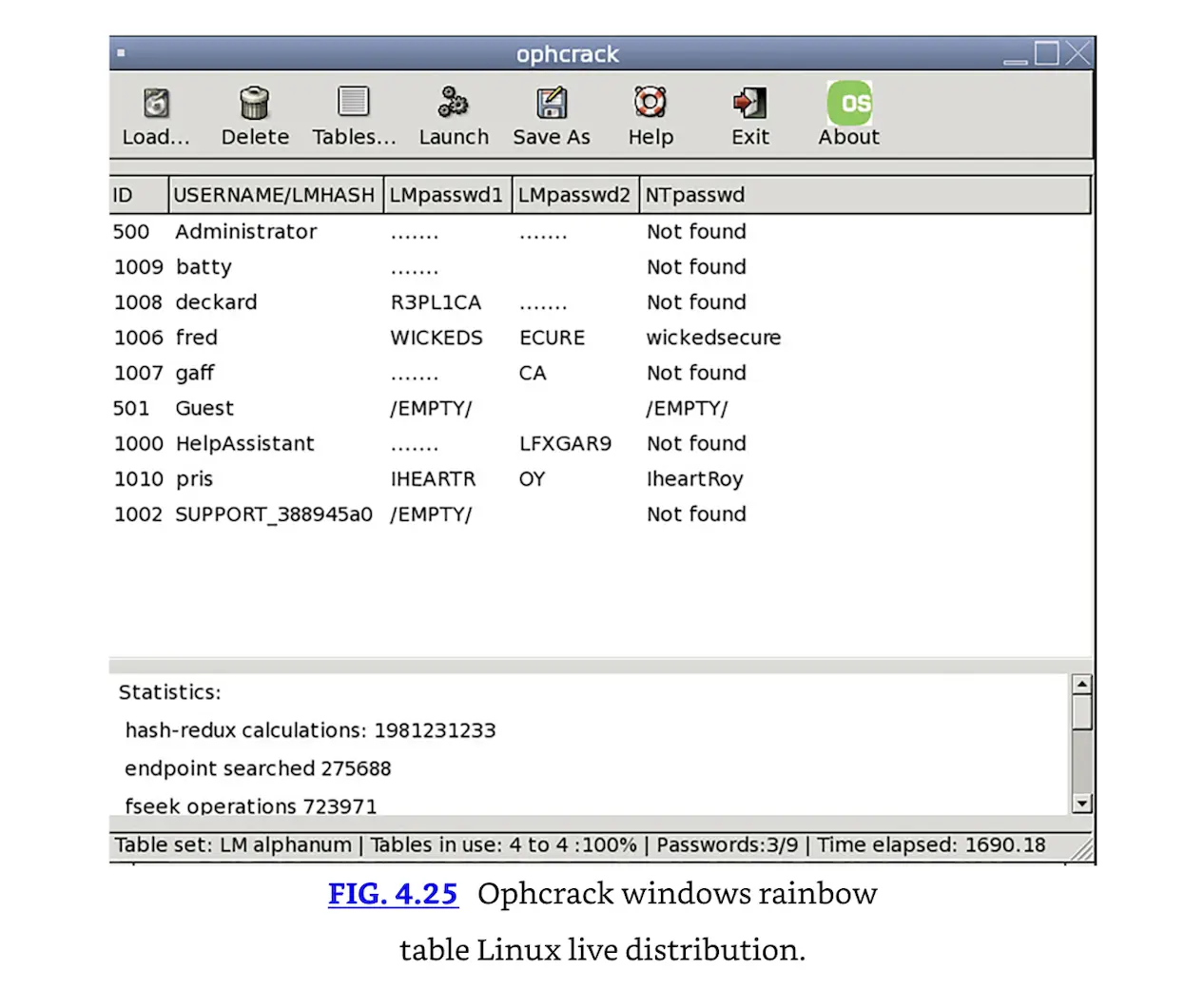 Ophcrack windows rainbow table Linux live distribution.
Ophcrack windows rainbow table Linux live distribution.