Page141
Implementing Cryptography
Symmetric, asymmetric, and hash-based cryptography do not exist in a vacuum: they are applied in the real world, often in combination, to provide confidentiality, integrity, authentication, and non-repudiation.
Digital Signatures
Digital signatures are used to cryptographically sign documents. Digital signatures provide non-repudiation, which includes authentication of the identity of the signer, and proof of the document’s integrity (proving the document did not change). This means the sender cannot later deny (or repudiate) signing the document.
Roy wants to send a digitally signed email to Rick. Roy writes the email, which is the plaintext. He then uses the SHA-1 hash function to generate a hash value of the plaintext. He then creates the digital signature by encrypting the hash with his RSA private key. Fig. 4.26 shows this process. Roy then attaches the signature to his plaintext email and hits send.
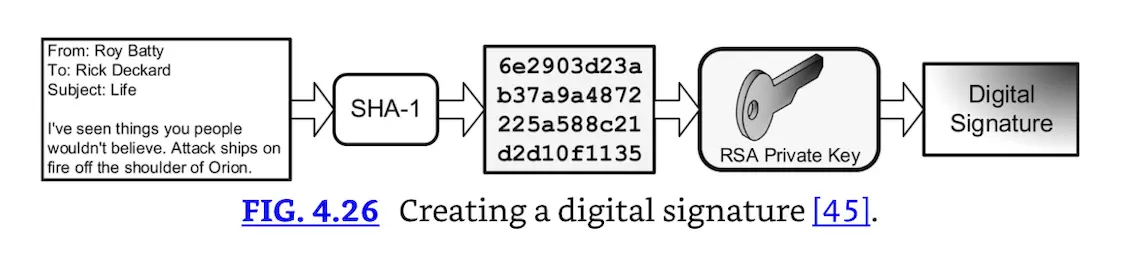 Creating a digital signature [45].
Creating a digital signature [45].
Rick receives Roy’s email and generates his own SHA-1 hash value of the plaintext email. Rick then decrypts the digital signature with Roy’s RSA public key, recovering the SHA-1 hash Roy generated. Rick then compares his SHA-1 hash with Roy’s. Fig. 4.27 shows this process.
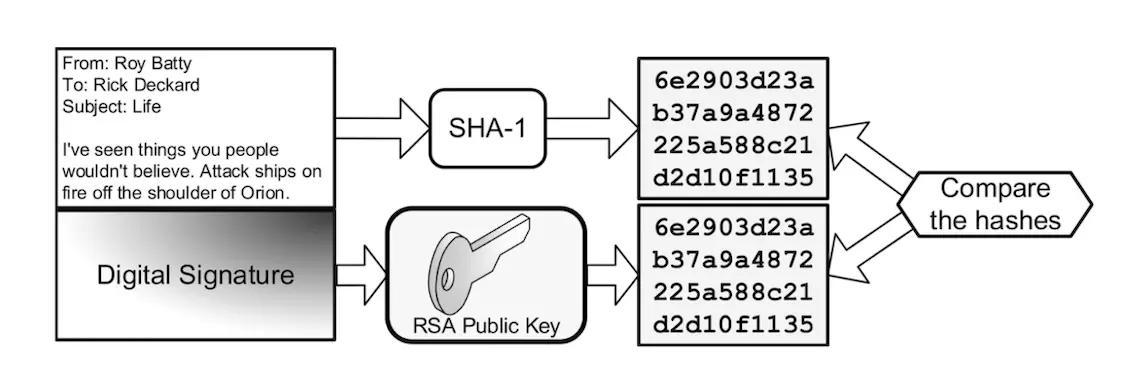 Verifying a digital signature.
Verifying a digital signature.
If the two hashes match, Rick knows several things:
- Roy must have sent the email (only Roy knows his private key). This authenticates Roy as the sender.
- The email did not change. This proves the integrity of the email.
If the hashes match, Roy cannot later deny having signed the email. This is non-repudiation. If the hashes do not match, Rick knows either Roy did not send it, or that the email’s integrity was violated.
Note
Digital signatures provide authentication and integrity, which forms non-repudiation. They do not provide confidentiality: the plaintext remains unencrypted.
Message Authenticate Code
A Message Authentication Code (MAC) is a hash function that uses a key. A common MAC implementation is Cipher Block Chaining Message Authentication Code (CBC-MAC), which uses CBC mode of a symmetric block cipher such as DES to create a MAC. Message Authentication Codes provide integrity and authenticity (proof that the sender possesses the shared key).
HMAC
A Hashed Message Authentication Code (HMAC) combines a shared key with hashing. IPsec uses HMACs (see below).
Two parties must pre-share a key. Once shared, the sender uses XOR to combine the plaintext with a shared key, and then hashes the output using an algorithm such as MD5 (called HMAC-MD5) or SHA-1 (called HMAC-SHA-1). That hash is then combined with the key again, creating an HMAC.
The receiver combines the same plaintext with the shared key locally, and then follows the same process described above, resulting in a local HMAC. The receiver compares that with the sender’s HMAC. If the two HMACs match, the sender is authenticated (this proves the sender knows the shared key), and the message’s integrity is assured (the message has not changed).