Page145
S/MIME
MIME (Multipurpose Internet Mail Extensions) provides a standard way to format email, including characters, sets, and attachments. S/MIME (Secure/ MIME) leverages PKI to encrypt and authenticate MIME-encoded email. The client or client’s email server (called an S/MIME gateway) may perform the encryption.
Escrowed Encryption
Escrowed encryption means a third-party organization holds a copy of a public/private key pair. The private key is often divided into two or more parts, each held in escrow by different trusted third-party organizations, which will only release their portion of the key with proper authorization, such as a court order. This provides separation of duties.
One goal of escrowed encryption is to offer a balance between an individual’s privacy, and the needs of law enforcement. Another goal is to ensure that encrypted data is recoverable in the event of key loss or employee termination.
Clipper Chip
The Clipper Chip was the name of the technology used in the Escrowed Encryption Standard (EES), an effort announced in 1993 by the United States government to deploy escrowed encryption in telecommunications devices. The effort created a media firestorm, and was abandoned by 1996.
The Clipper Chip used the Skipjack algorithm, a symmetric cipher that uses an 80-bit key. The algorithm was originally classified as secret. The secrecy of the algorithm was another controversial issue: secrecy of an algorithm does not provide cryptographic strength, and secret ciphers are often found to be quite insecure. Skipjack was later declassified in 1998 (after the Clipper Chip effort had been abandoned).
Steganography
Steganography is the science of hidden communication. The name is based on the Greek words “steganos” and “graphein,” which mean covered and write, or concealed writing. Encryption may provide confidentiality to a radio transmission, for example, but the communication itself is not hidden; only the meaning is concealed. Steganography hides the fact that communication is taking place.
The ancient Greek historian Herodotus documented the first use of steganography in the Histories of Herodotus. Herodotus described shaving a slave’s head, tattooing instructions on it, waiting for the hair to grow back, and sending the slave across enemy lines. Another method hid a message inside a rabbit’s stomach.
Modern steganography hides information inside data files, such as images. An 8-bit bitmap has 256 colors, for example. Say two different white pixels (called W0 and W1) in the image appear identical to the naked eye. You may encode a message by treating W0 and W1 as a bit stream.
Assume the file has a sequence of pixels in this order: W1, W1, W1, W1, W0, W0, W0, W1. You would like to encode “10101010” in the image. Treat W0 as binary 0 and W1 as binary 1. Then flip the pixels accordingly, resulting in W1, W0, W1, W0, W1, W0, W1, W0. Fig. 4.28 shows the process. A white arrow means the pixel was unchanged; black arrows represent changed pixels.
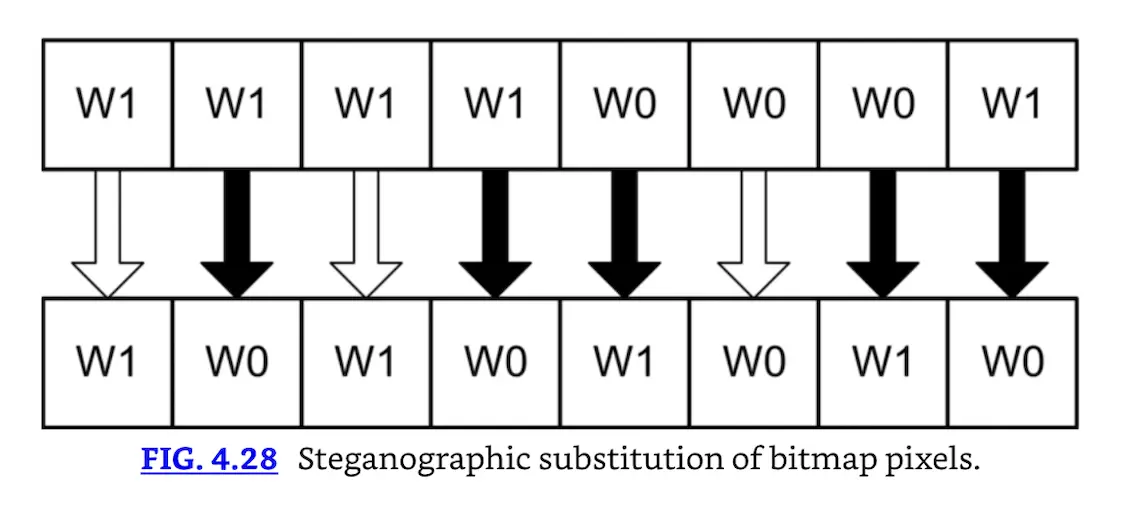 Steganographic substitution of bitmap pixels.
Steganographic substitution of bitmap pixels.
The image now contains the hidden message “10101010,” though it appears the same to the naked eye (and the size has not changed). The integrity of the image has changed. This method is called Substitution. Other methods include injection (add data to the file, creating a larger file) and new file creation. Substitution and Injection require a host file; new file creation creates a new file, as the name implies.
Messages that are hidden via steganography are often encrypted first, providing both confidentiality of the data and secrecy of the communication.