Page170
-
You are surfing the Web via a wireless network. Your wireless connection becomes unreliable, so you plug into a wired network to continue surfing. While you changed physical networks, your browser required no change. What security feature allows this?
A. Abstraction
B. Hardware Segmentation
C. Layering
D. Process Isolation -
A criminal deduces that an organization is holding an offsite meeting and has few people in the building, based on the low traffic volume to and from the parking lot, and uses the opportunity to break into the building to steal laptops. What type of attack has been launched?
A. Aggregation
B. Emanations
C. Inference
D. Maintenance Hook -
EMI issues such as crosstalk primarily impact which aspect of security?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication -
What is the most important goal of fire suppression systems?
A. Preservation of critical data
B. Safety of personnel
C. Building integrity
D. Quickly extinguishing a fire -
Which of the following statements regarding containers and virtual machines is true?
A. Both containers and virtual machines share the same kernel
B. Virtual machines share the same kernel; containers use their own kernel
C. Containers share the same kernel; virtual machines use their own kernel
D. Both containers and virtual machines use their own kernel -
Non-repudiation is best described as what?
A. Proving a user performed a transaction
B. Proving a transaction did not change
C. Authenticating a transaction
D. Proving a user performed a transaction that did not change -
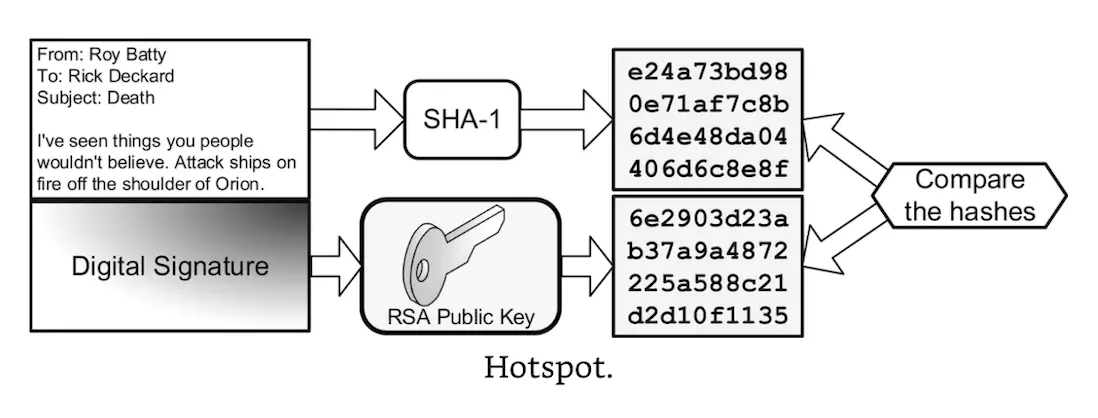
Hotspot: you receive the following signed email from Roy Batty. You determine that the email is not authentic, or has changed since it was sent. Click on the locally generated message digest that proves the email lacks non-repudiation.