Page204
Virtual SAN
Storage Area Networks have historically tended to be rather proprietary and used dedicated hardware and protocols that did not easily interoperate. Though many SAN implementations now leverage protocols such as FCoE, FCIP, or iSCSI that can allow for converged traditional networking technologies and protocols, the scalability and security of the Storage Area Networking has often proven cumbersome.
Traditional approaches to storage security often required hard-coding changes at switches or the HBAs to achieve access control. One approach to a virtual SAN feels analogous to the switching concept of VLANs and tries to allow for a conceptually simplistic approach to isolation within the SAN. This concept of the virtual SAN as analogous to VLANs is most commonly employed by networking vendors.
The concept of a virtual SAN is not limited to simply security considerations from networking vendors. Much recent use of the term virtual SAN leans heavily on the virtual side of the phrase. Virtualization vendors employ the term virtual SAN to imply an approach to the SAN that allows for more rapid provisioning of virtualized storage. Beyond provisioning, virtualization vendors tout the virtual SAN as a means to leverage virtualization to afford simpler linear scalability to the storage area network.
VoIP
Voice over Internet Protocol (VoIP) carries voice via data networks, a fundamental change from analog POTS (Plain Old Telephone Service), which remains in use after over 100 years. VoIP brings the advantages of packet-switched networks, such as lower cost and resiliency, to the telephone.
Recently, many organizations have maintained at least two distinct networks: a phone network and a data network, each with associated maintenance costs. The reliability of packet-switched data networks has grown as organizations have made substantial investments. With the advent of VoIP, many organizations have lowered costs by combining voice and data services on packet-switched networks.
Common VoIP protocols include Real-time Transport Protocol (RTP), designed to carry streaming audio and video. VoIP protocols such as RTP rely upon session and signaling protocols including SIP (Session Initiation Protocol, a signaling protocol) and H.323. SRTP (Secure Real-time Transport Protocol) may be used to provide secure VoIP, including confidentiality, integrity, and secure authentication. SRTP uses AES for confidentiality and SHA-1 for integrity.
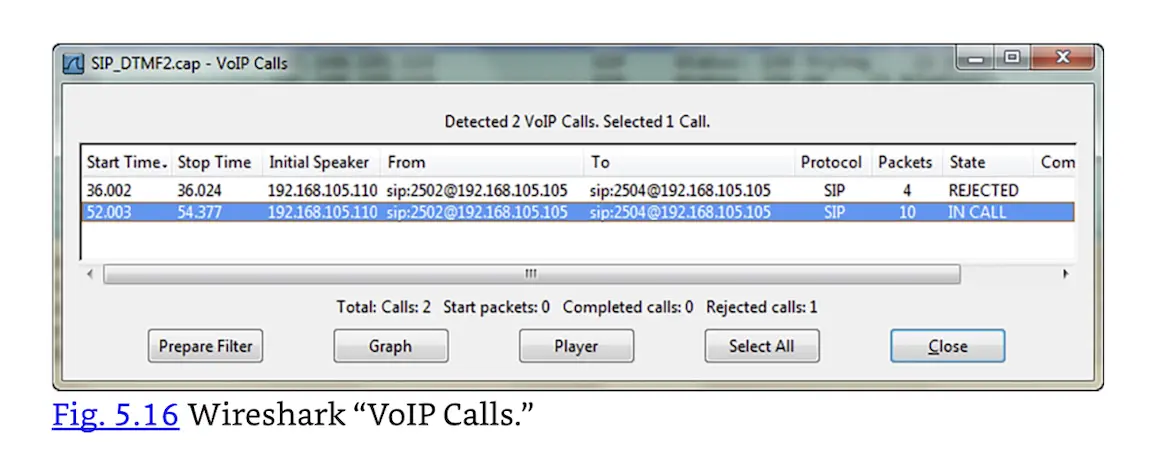
While VoIP can provide compelling cost advantages (especially for new sites, without a large legacy voice investment), there are security concerns. If the network goes down, both voice and network data go down. Also, there is no longer a true “out of band” channel for wired voice. If an attacker has compromised a network, they may be able to compromise the confidentiality or integrity of the VoIP calls on that network. Many VoIP protocols, such as RTP, provide little or no security by default. In that case, eavesdropping on a VoIP call is as simple as sniffing with a tool like Wireshark (a high-quality free network protocol analyzer, see https://www.wireshark.org), selecting the “Telephony → VoIP Calls” menu, choosing a call and pressing “Player,” as shown in Fig. 5.16.
 Wireshark “VoIP Calls.”
Wireshark “VoIP Calls.”
Organizations that deploy VoIP must ensure reliability by making sufficient investments in their data networks, and in staff expertise required to support them. In the event of network compromise, use other methods such as cell phones for out-of-band communication. Finally, any VoIP traffic sent via insecure networks should be secured via SRTP, or other methods such as IPsec. Never assume VoIP traffic is secure by default.