Page212
Secure Network Devices and Protocols
Let us look at network devices ranging from Layer 1 hubs through Application-Layer Proxy firewalls that operate up to Layer 7. Many of these network devices, such as routers, have protocols dedicated to their use, such as routing protocols.
Repeaters and Hubs
Repeaters and hubs are Layer 1 devices. A repeater receives bits on one port, and “repeats” them out the other port. The repeater has no understanding of protocols; it simply repeats bits. Repeaters are often used to extend the length of a network.
A hub is a repeater with more than two ports. It receives bits on one port and repeats them across all other ports.
Hubs were quite common before switches became common and inexpensive. Hubs provide no traffic isolation and have no security: all nodes see all traffic sent by the hub. Hubs provide no confidentiality or integrity; an attacker connected to a hub may read and potentially alter traffic sent via the hub.
Hubs are also half-duplex devices: they cannot send and receive simultaneously. Any device connected to a hub will negotiate to half-duplex mode, which can cause network congestion. Hubs also have one “collision domain”: any node may send colliding traffic with another (for more information on collisions, see the previous “CSMA” section). The lack of security, half-duplex mode, and large collision domain make hubs unsuitable for most modern purposes.
Bridges
Bridges and switches are Layer 2 devices. A bridge has two ports and connects network segments together. Each segment typically has multiple nodes, and the bridge learns the MAC addresses of nodes on either side. Traffic sent from two nodes on the same side of the bridge will not be forwarded across the bridge. Traffic sent from a node on one side of the bridge to the other side will forward across. The bridge provides traffic isolation and makes forwarding decisions by learning the MAC addresses of connected nodes.
In Fig. 5.18, traffic sent from Computer 1 to Computer 2 will not forward across the bridge. Traffic sent from Computer 1 to Computer 3 will be forwarded across the bridge.
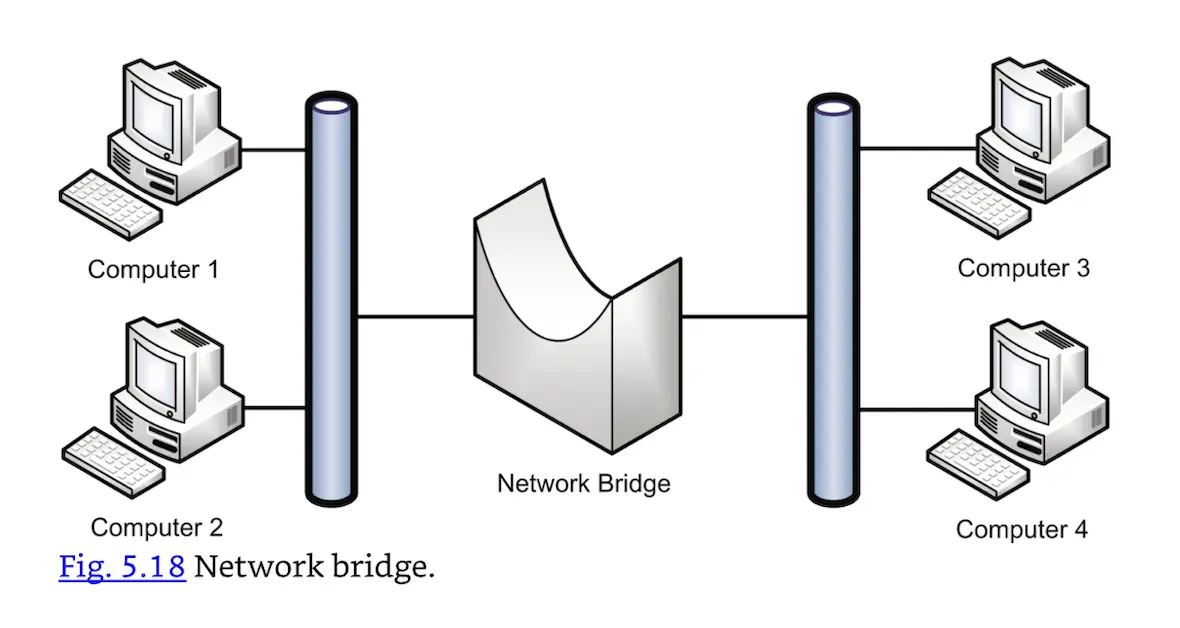 Network bridge.
Network bridge.
A bridge has two collision domains. A network protocol analyzer (informally called a “sniffer”) on the right side of the network shown in Fig. 5.18 can sniff traffic sent to or from Computers 3 and 4, but not sniff Computer 1 or 2 traffic (unless sent to Computers 3 or 4).