Page221
802.1X and EAP
802.1X is “Port Based Network Access Control,” and includes EAP (Extensible Authentication Protocol). EAP is an authentication framework that describes many specific authentication protocols. EAP is designed to provide authentication at Layer 2 (it is “port based,” like ports on a switch), before a node receives an IP address. It is available for both wired and wireless, but is more commonly deployed on WLANs.
The major 802.1X roles are:
- Supplicant: An 802.1X client
- Authentication Server (AS): A server that authenticates a supplicant
- Authenticator: A device such as an access point that allows a supplicant to authenticate and connect
Exam Warning: Do not confuse 802.1X (EAP) with 802.11 (Wireless). EAP addresses many issues, including the “roaming infected laptop” problem. A user with an infected laptop plugs into a typical office network and requests an IP address from a DHCP server. Once given an IP, the malware installed on the laptop begins attacking other systems on the network.
By the time the laptop is able to request an IP address, it is already in a position to cause harm on the network, including confidentiality, integrity, and availability attacks. This problem is most acute on WLANs (where an outside laptop 100 feet away from a building may be able to access the network). Ideally, authentication should be required before the laptop can join the network: EAP does exactly this.
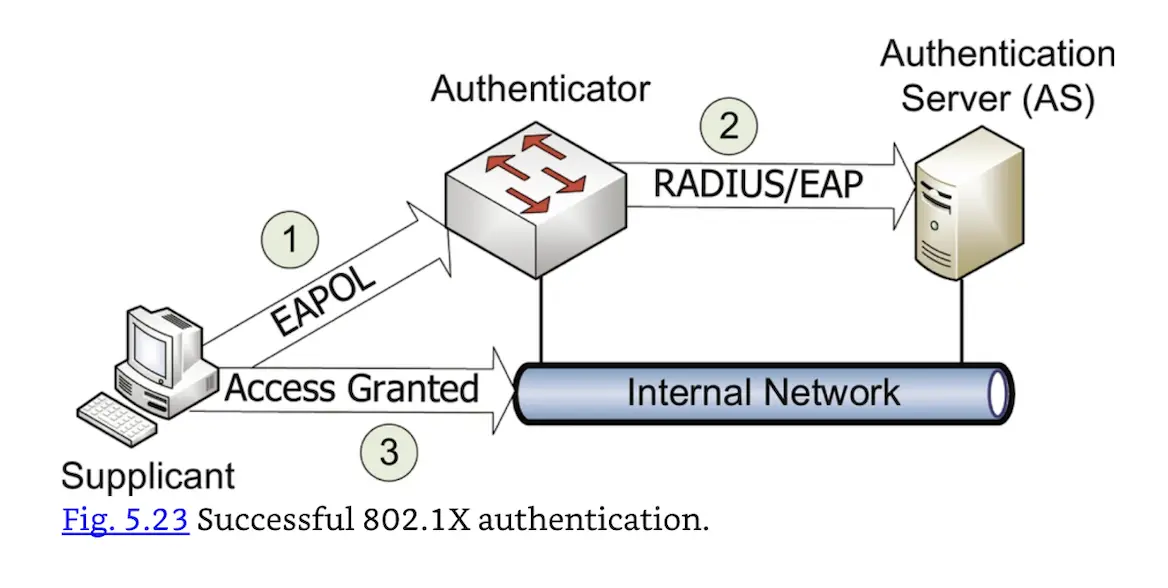 Successful 802.1X authentication.
Successful 802.1X authentication.
Fig. 5.23 shows a supplicant successfully authenticating and connecting to an internal network. Step 1 shows the Supplicant authenticating via EAPOL (EAP Over LAN), a Layer 2 EAP implementation. Step 2 shows the Authenticator receiving the EAPOL traffic and using RADIUS or Diameter to carry EAP traffic to the Authentication Server (AS). Step 3 shows the Authenticator allowing Supplicant access to the internal network after successful authentication.
There are many types of EAP; we will focus on EAP-MD5, LEAP, EAP-FAST, EAP-TLS, EAP-TTLS, and PEAP:
- EAP-MD5 is one of the weakest forms of EAP. It offers client-server authentication only (all other forms of EAP discussed in this section support mutual authentication of client and server); this makes it vulnerable to man-in-the-middle attacks. EAP-MD5 is also vulnerable to password-cracking attacks.
- LEAP (Lightweight Extensible Authentication Protocol) is a Cisco-proprietary protocol released before 802.1X was finalized. LEAP has significant security flaws and should not be used.
- EAP-FAST (EAP-Flexible Authentication via Secure Tunneling) was designed by Cisco to replace LEAP. It uses a Protected Access Credential (PAC), which acts as a pre-shared key.
- EAP-TLS (EAP-Transport Layer Security) uses PKI, requiring both server-side and client-side certificates. EAP-TLS establishes a secure TLS tunnel used for authentication. EAP-TLS is very secure due to the use of PKI but is complex and costly for the same reason. The other major versions of EAP attempt to create the same TLS tunnel without requiring a client-side certificate.
- EAP-TTLS (EAP Tunneled Transport Layer Security), developed by Funk Software and Certicom, simplifies EAP-TLS by dropping the client-side certificate requirement, allowing other authentication methods (such as password) for client-side authentication. EAP-TTLS is thus easier to deploy than EAP-TLS, but less secure when omitting the client-side certificate.
- PEAP (Protected EAP), developed by Cisco Systems, Microsoft, and RSA Security, is like (and may be considered a competitor to) EAP-TTLS, including not requiring client-side certificates.