Page235
Dictionary Attacks
A dictionary attack uses a word list: a predefined list of words, and each word in the list is hashed. If the cracking software matches the hash output from the dictionary attack to the password hash, the attacker has successfully identified the original password.
Note:
Attackers will often tune their dictionary to their target, adding a Spanish dictionary to their word list for a target organization with Spanish speakers, or even a Klingon dictionary for an organization with Star Trek fans. Packet Storm Security maintains multiple dictionaries at https://packetstormsecurity.com/Crackers/wordlists/.
Because a dictionary attack can be performed quickly, many organizations require users to create passwords that have a special character, number, capital letter, and be eight characters or greater. Fig. 6.2 shows the use of a password cracker, John the Ripper (https://www.openwall.com/john/), against the previously acquired details from the SAM file shown in Fig. 6.1. Even running a simple dictionary attack quickly reveals the user deckard’s password as “replicant.” Access to the SAM file (Windows) and shadow file (UNIX/Linux) should be restricted.
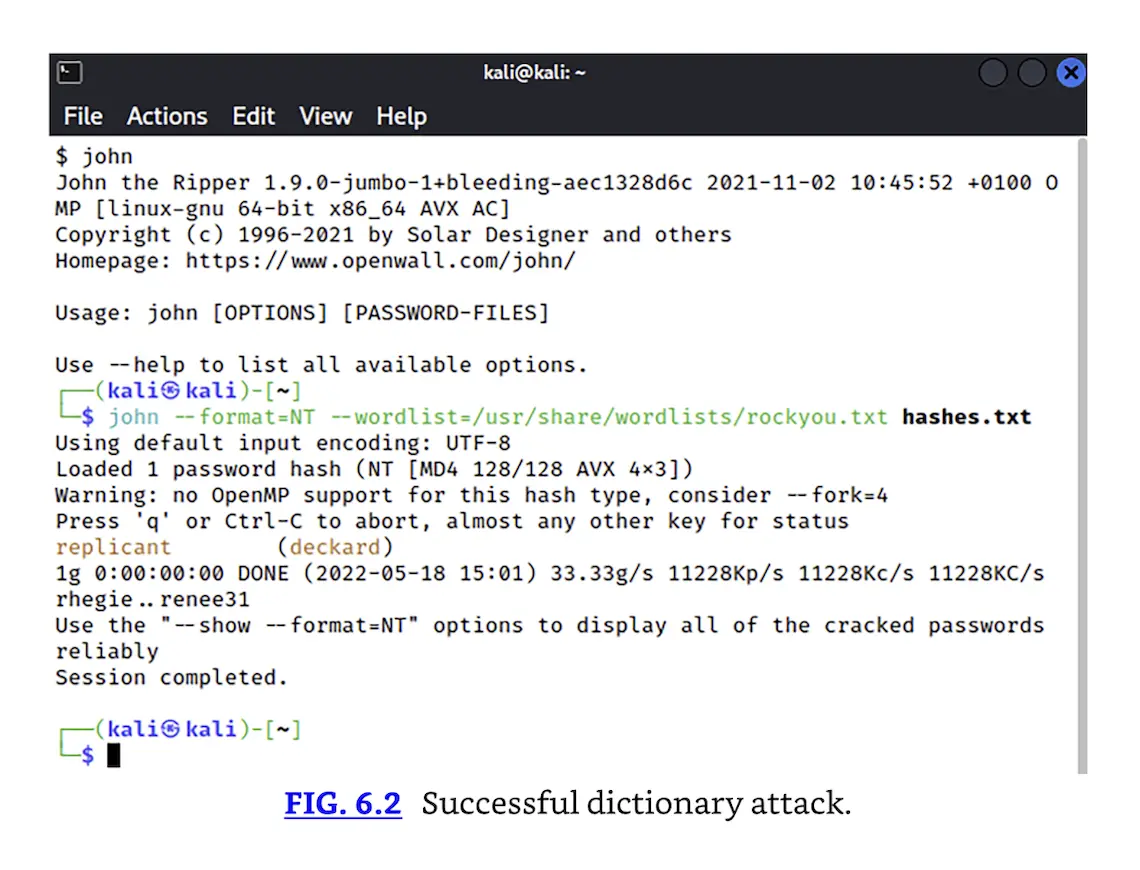 Successful dictionary attack.
Successful dictionary attack.