Page238
Type 2 Authentication: Something You Have
Type 2 authentication (something you have) requires that users possess something, such as a token, which proves they are an authenticated user. A token is an object that helps prove an identity claim. The simplest example of a token is a set of car keys. Possessing the car keys means one has access to the car. Other examples of tokens include credit cards, bank ATM cards, smart cards, and paper documents. ATM cards also use a PIN to access a user’s bank account, increasing the overall security of the user’s account.
Synchronous Dynamic Token
Synchronous dynamic tokens use time or counters to synchronize a displayed token code with the code expected by the authentication server: the codes are synchronized.
Time-based synchronous dynamic tokens display dynamic token codes that change frequently, such as every 60 seconds. The dynamic code is only good during that window. The authentication server knows the serial number of each authorized token, the user it is associated with, and the time. It can predict the dynamic code on each token using these three pieces of information. RSA SecurID is an example of a hardware-based synchronous dynamic token. Google Authenticator, shown in Fig. 6.4, is an example of a software-based synchronous dynamic token (also called a soft token).
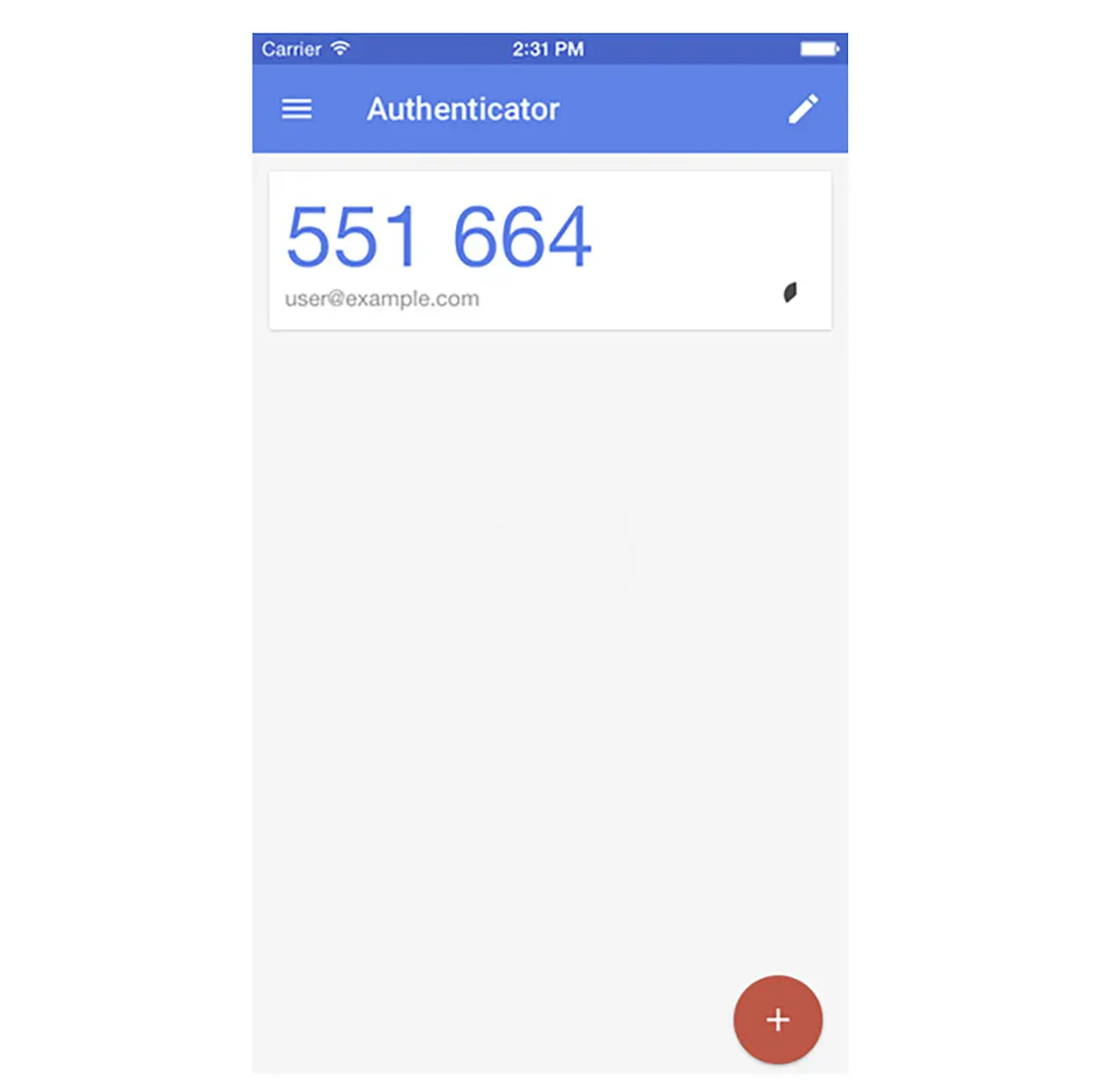 Google Authenticator [4].
Google Authenticator [4].
Counter-based synchronous dynamic tokens use a simple counter: the authentication server expects token code 1, and the user’s token displays the same code 1. Once used, the token displays the second code, and the server also expects token code 2.
In both cases, users typically authenticate by typing their username, their PIN or password (something they know), and the dynamic token code (something they have). This method uses strong authentication: the token is useless without the PIN, and the PIN is useless without the token.