Page249
Kerberos Operational Steps
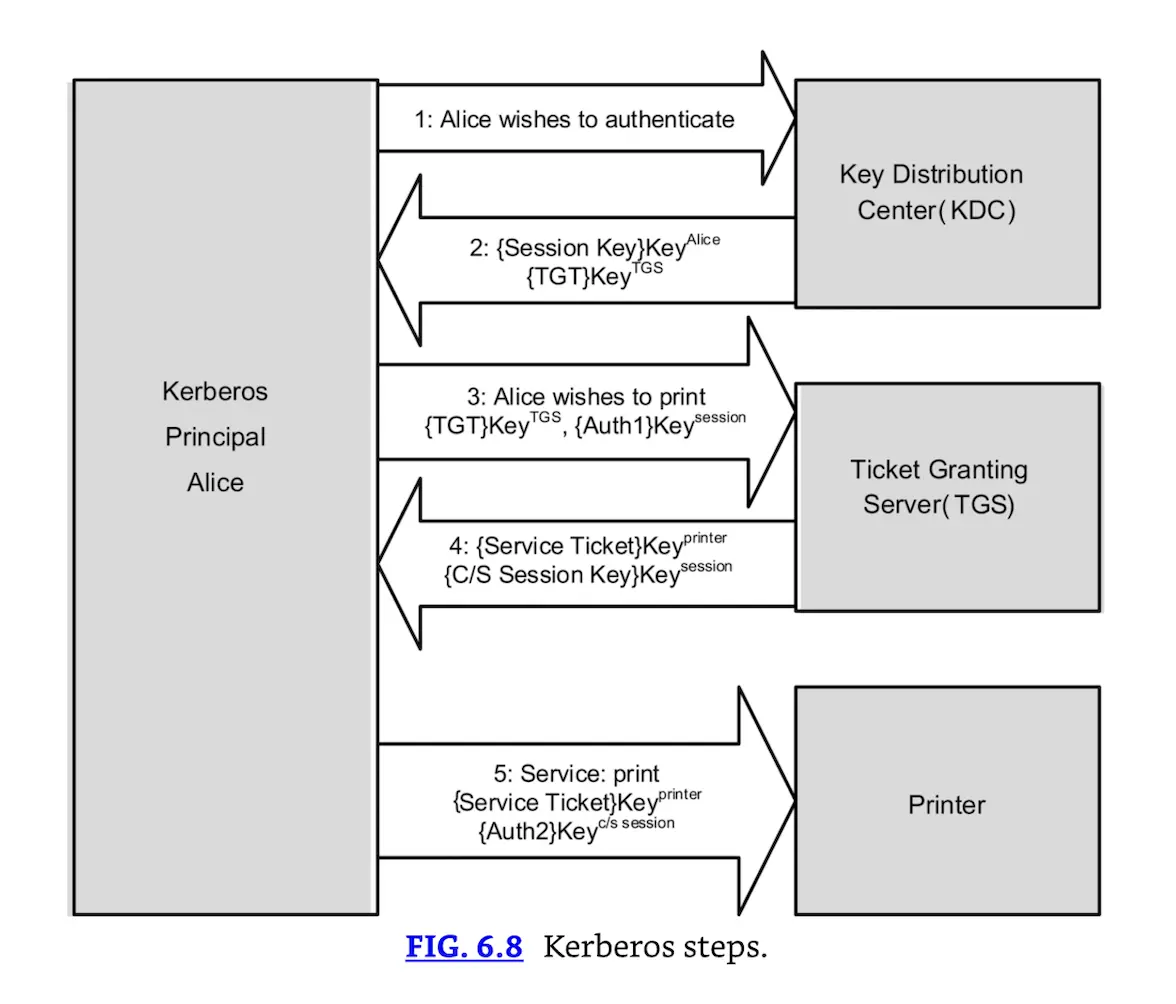
A Kerberos principal, a client run by user Alice, wishes to access a printer. Alice may print after taking these five (simplified) steps:
- Kerberos Principal Alice contacts the KDC (Key Distribution Center, which acts as an authentication server), requesting authentication.
- The KDC sends Alice a session key, encrypted with Alice’s secret key. The KDC also sends a TGT (Ticket Granting Ticket), encrypted with the TGS’s secret key.
- Alice decrypts the session key and uses it to request permission to print from the TGS (Ticket Granting Service).
- Seeing Alice has a valid session key (and therefore has proven her identity claim), the TGS sends Alice a C/S session key (second session key) to use to print. The TGS also sends a service ticket, encrypted with the printer’s key.
- Alice connects to the printer. The printer, seeing a valid C/S session key, knows Alice has permission to print, and also knows that Alice is authentic.
This process is summarized in Fig. 6.8.
 Kerberos steps.
Kerberos steps.
The session key in step 2 of Fig. 6.8 is encrypted with Alice’s key (represented as “{Session Key}KeyAlice”). Also note that the TGT is encrypted with the TGS’s key: Alice cannot decrypt the TGT (only the TGS can); she simply sends it to the TGS. The TGT contains a number of items, including a copy of Alice’s session key. This is how the TGS knows that Alice has a valid session key (which proves Alice is authenticated).
Note:
Many sites run both the KDC and TGS services on one system, but they may be run on separate systems. It is helpful to think of them as independent systems for the exam.
The TGT is good for a site-selected specific lifetime, often set to 10 hours (the length of a workday, plus a couple of hours). This allows a typical user to authenticate once, and access network resources for the lifetime of the ticket. Kerberos is stateless for this reason: once Alice has a TGT, she may use it for its lifetime, even if the KDC goes offline. Also, the TGS can allow Alice to print without consulting the KDC: everything the TGS needs to know is contained in the traffic Alice sends, including the TGT and the first authenticator.
The same is true for the service ticket Alice sends to the printer. It is encrypted with the printer’s key, and contains a copy of the client/server session key. Alice cannot decrypt it, and simply passes it back to the printer. This allows the printer to make its decision based entirely on what Alice sends, without consulting the KDC or the TGS.
Note
This section (and the exam) describes “plain vanilla” Kerberos, not specific vendor implementations such as Kerberos within Microsoft Windows Active Directory.