Page293
Many incident handling methodologies treat containment, eradication, and recovery as three distinct steps, as we will in this book. Other names for each step are sometimes used; the current exam lists a 7-step lifecycle, but (curiously) omits the first step in most incident handling methodologies: preparation. Perhaps preparation is implied, like the identification portion of AAA systems. We will therefore cover eight steps, mapped to the current exam:
- Preparation
- Detection (aka Identification)
- Response (aka Containment)
- Mitigation (aka Eradication)
- Reporting
- Recovery
- Remediation
- Lessons Learned (aka Post-incident Activity, Post Mortem, or Reporting)
It is important to remember that the final step feeds back into the first step, as shown previously in Fig. 8.3. An organization may determine that staff members were insufficiently trained to handle incidents during the lessons learned phase. That lesson is then applied to continued preparation, where staff members would be properly trained.
Preparation
The preparation phase includes steps taken before an incident occurs. These include training, writing incident management policies and procedures, providing tools such as laptops with sniffing software, crossover cables, original OS media, and removable drives. Preparation should include anything that may be required to handle an incident, or which will make incident response faster and more effective. One preparation step is preparing an incident handling checklist. Fig. 8.4 is an incident handling checklist from NIST Special Publication 800-61r2.
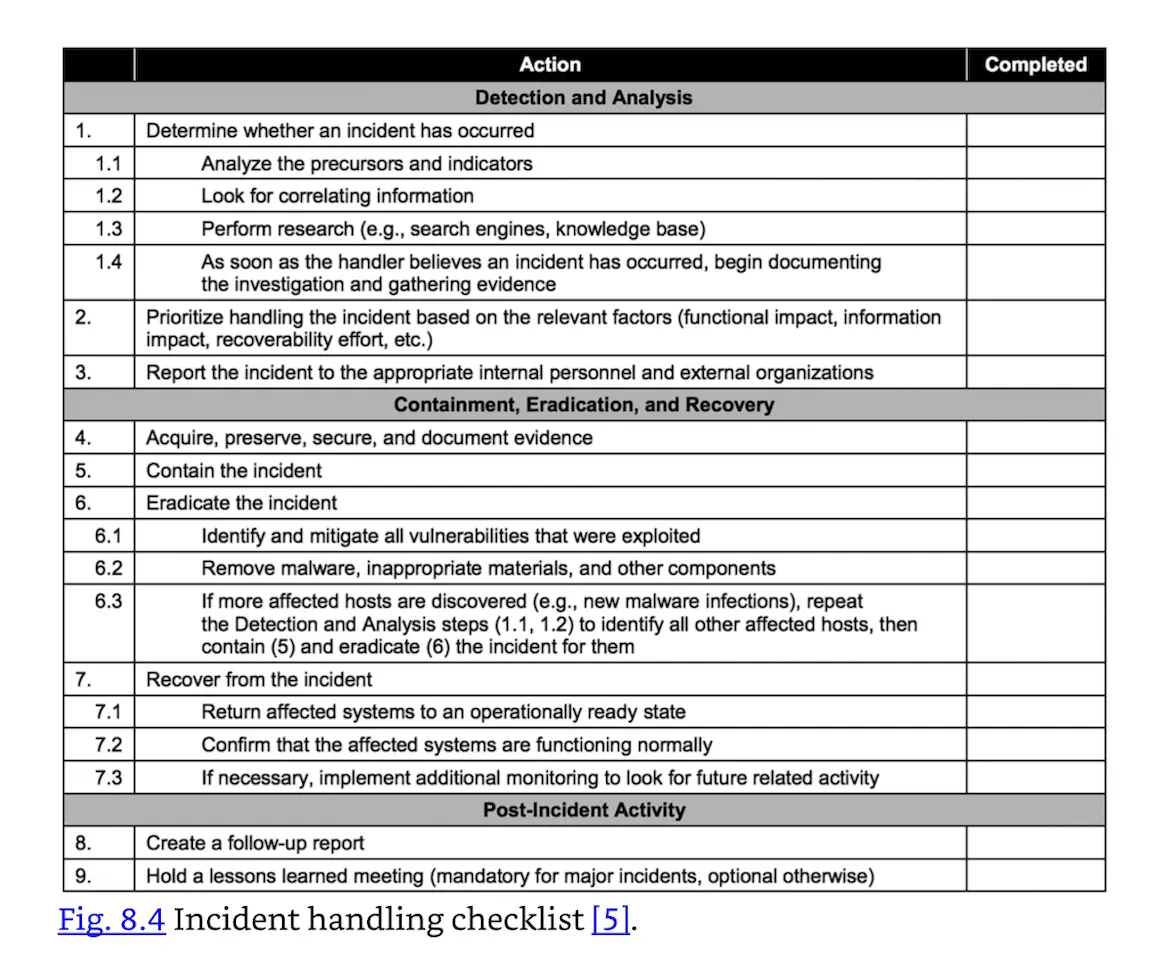 Incident handling checklist [5].
Incident handling checklist [5].