Page297
Operational Preventive and Detective Controls
Many preventive and detective controls require higher operational support, and are a focus of daily operations security. For example: routers and switches tend to have comparatively low operational expenses (OPEX). Other controls, such as NIDS and NIPS, antivirus, and application whitelisting have comparatively higher operational expenses, and are a focus in this domain.
Firewalls
Firewalls filter traffic between networks. TCP/IP packet filter and stateful firewalls make decisions based on layers 3 and 4 (IP addresses and ports). Proxy firewalls can also make decisions based on layers 5–7. Firewalls are multi-homed: they have multiple NICs connected to multiple different networks.
Packet Filter
A packet filter is a simple and fast firewall. It has no concept of “state”: each filtering decision must be made on the basis of a single packet. There is no way to refer to past packets to make current decisions.
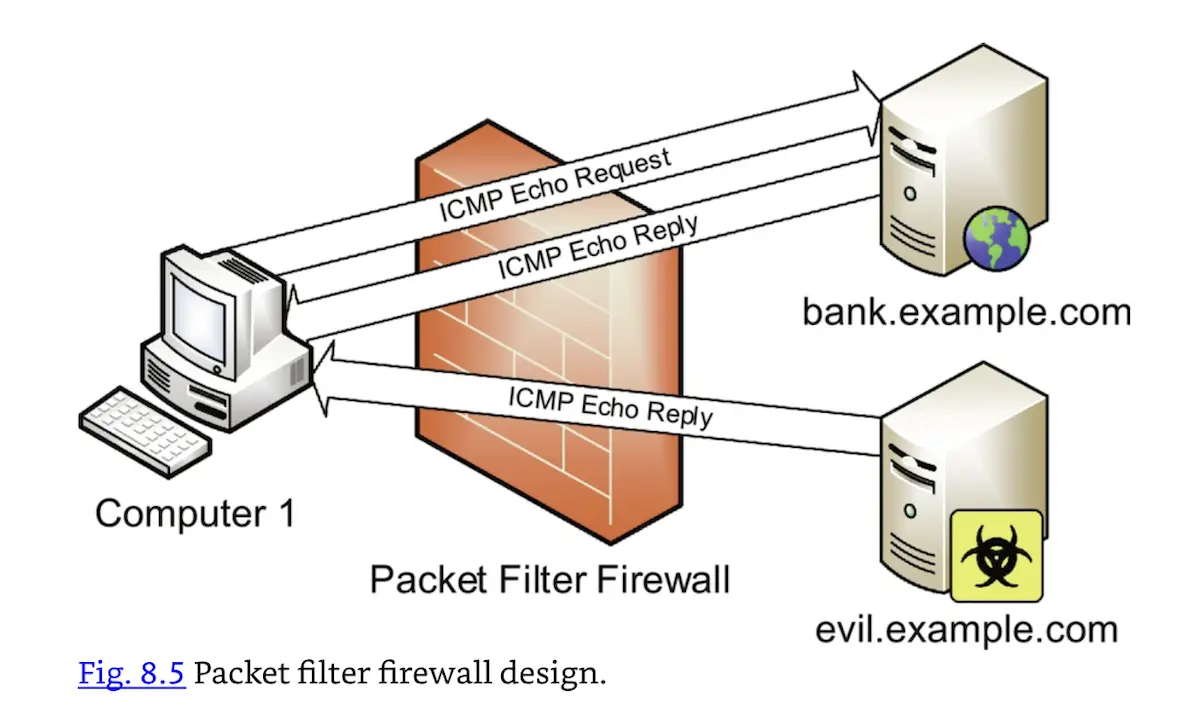
The lack of state makes packet filter firewalls less secure, especially for sessionless protocols like UDP and ICMP. In order to allow ping via a firewall, both ICMP Echo Requests and Echo Replies must be allowed, independently: the firewall cannot match a previous request with a current reply. All Echo Replies are usually allowed, based on the assumption that there must have been a previous matching Echo Request.
The packet filtering firewall shown in Fig. 8.5 allows outbound ICMP echo requests and inbound ICMP echo replies. Computer 1 can ping bank.example.com. The problem: an attacker at evil.example.com can send unsolicited echo replies, which the firewall will allow.
 Packet filter firewall design.
Packet filter firewall design.
UDP-based protocols suffer similar problems. DNS uses UDP port 53 for small queries, so packet filters typically allow all UDP DNS replies on the assumption that there must have been a previous matching request.