Page301
DMZ Networks and Screened Subnet Architecture
A DMZ is a Demilitarized Zone network; the name is based on real-world military DMZ, such as the DMZ between North Korea and South Korea. A DMZ is a dangerous “no-man’s land”: this is true for both military and network DMZ.
Any server that receives traffic from an untrusted source such as the Internet is at risk of being compromised. We use defense-in-depth mitigation strategies to lower this risk, including patching, server hardening, and NIDS, but some risk always remains.
Network servers that receive traffic from untrusted networks such as the Internet should be placed on DMZ networks for this reason. A DMZ is designed with the assumption that any DMZ host may be compromised: the DMZ is designed to contain the compromise, and prevent it from extending into internal trusted networks. Any host on a DMZ should be hardened. Hardening should consider attacks from untrusted networks, as well as attacks from compromised DMZ hosts.
A “classic” DMZ uses two firewalls, as shown in Fig. 8.10. This is called screened subnet dual firewall design: two firewalls screen the DMZ subnet.
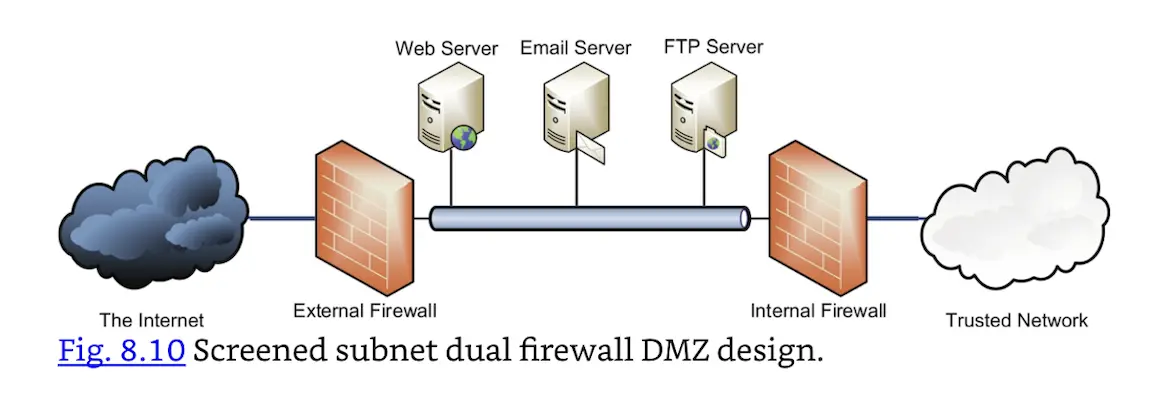 Screened subnet dual firewall DMZ design.
Screened subnet dual firewall DMZ design.
A single-firewall DMZ uses one firewall, as shown in Fig. 8.11. This is sometimes called a “three-legged” DMZ.
 Single firewall DMZ design.
Single firewall DMZ design.
The single firewall design requires a firewall that can filter traffic on all interfaces: untrusted, trusted, and DMZ. Dual firewall designs are more complex, but considered more secure. In the event of compromise due to firewall failure, a dual firewall DMZ requires two firewall failures before the trusted network is exposed. Single firewall design requires one failure.
Note: The term “DMZ” alone implies a dual firewall DMZ.