Page307
NIDS and NIPS
A Network-based Intrusion Detection System (NIDS) detects malicious traffic on a network. NIDSs usually require promiscuous network access in order to analyze all traffic, including all unicast traffic. NIDSs are passive devices that do not interfere with the traffic they monitor; Fig. 8.12 shows a typical NIDS architecture. The NIDS sniffs the internal interface of the firewall in read-only mode and sends alerts to a NIDS Management server via a different (read/write) network interface.
 NIDS architecture.
NIDS architecture.
The difference between a NIDS and a NIPS is that the NIPS alters the flow of network traffic. There are two types of NIPS: active response and inline. Architecturally, an active response NIPS is like the NIDS in Fig. 8.12; the difference is the monitoring interface is read/write. The active response NIPS may “shoot down” malicious traffic via a variety of methods, including forging TCP RST segments to source or destination (or both), or sending ICMP port, host, or network unreachable to source.
Snort, a popular open-source NIDS and NIPS (see www.snort.org), has the following active response rules:
reset_dest: send TCP RST to destinationreset_source: send TCP RST to sourcereset_both: send TCP RST to both the source and destinationicmp_net: send ICMP network unreachable to sourceicmp_host: send ICMP host unreachable to sourceicmp_port: send ICMP port unreachable to sourceicmp_all: send ICMP network, host, and port unreachable to source
An inline NIPS is “in line” with traffic, playing the role of a layer 3–7 firewall by passing or allowing traffic, as shown in Fig. 8.13.
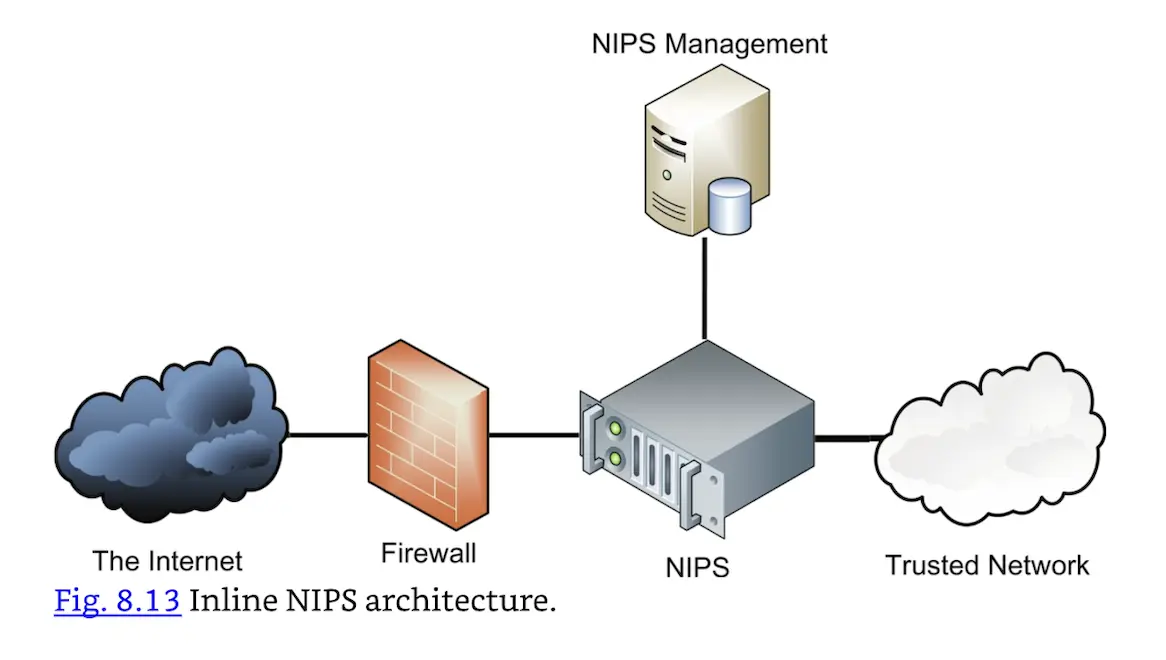 Inline NIPS architecture.
Inline NIPS architecture.
Note that a NIPS provides defense-in-depth protection in addition to a firewall; it is not typically used as a replacement. Also, a false positive by a NIPS is more damaging than one by a NIDS: legitimate traffic is denied, which may cause production problems. A NIPS usually has a smaller set of rules compared to a NIDS. For this reason, only the most trustworthy rules are used in a NIPS. A NIPS is not a replacement for a NIDS; many networks use both a NIDS and a NIPS.
HIDS and HIPS
Host-based Intrusion Detection Systems (HIDS) and Host-based Intrusion Prevention Systems (HIPS) are host-based cousins to NIDS and NIPS. They process information within the host. They may process network traffic as it enters the host, but the exam’s focus is usually on files and processes.
A well-known HIDS is Open Source Tripwire®, which was previously just called Tripwire before the company expanded its commercial offerings (see https://github.com/Tripwire/tripwire-open-source). Open Source Tripwire® protects system integrity by detecting changes to critical operating system files. Changes are detected through a variety of methods, including comparison of cryptographic hashes.
Pattern Matching
A Pattern Matching IDS works by comparing events to static signatures. Regarding the previously mentioned Log4Shell vulnerability, Crowdstrike notes “exploitation attempts can be detected by inspecting log files for the characteristic URL pattern ${jndi:ldap://}” [7]. Based on that information, the following pattern can be used to detect this type of attempted Log4Shell Log4j2 exploitation. If the string ${jndi:ldap://} appears in traffic to the organizations’ web servers: alert.
Pattern Matching works well for detecting known attacks, but usually fares poorly against new attacks.