Page374
NIST Special Publication 800-14 states: “Security, like other aspects of an IT system, is best managed if planned for throughout the IT system life cycle. There are many models for the IT system life cycle but most contain five basic phases: initiation, development/acquisition, implementation, operation, and disposal” [18]. Additional steps are often added, most critically the security plan, which is the first step of any SDLC. The following overview is summarized from NIST SP 800-14:
- Prepare a Security Plan: Ensure that security is considered during all phases of the IT system lifecycle, and that security activities are accomplished during each of the phases.
- Initiation: The need for a system is expressed and the purpose of the system is documented.
- Conduct a Sensitivity Assessment: Look at the security sensitivity of the system and the information to be processed.
- Development/Acquisition: The system is designed, purchased, programmed, or developed.
- Determine Security Requirements: Determine technical features (like access controls), assurances (like background checks for system developers), or operational practices (like awareness and training).
- Incorporate Security Requirements Into Specifications: Ensure that the previously gathered information is incorporated in the project plan.
- Obtain the System and Related Security Activities: May include developing the system’s security features, monitoring the development process itself for security problems, responding to changes, and monitoring threats.
- Implementation: The system is tested and installed.
- Install/Turn-On Controls: A system often comes with security features disabled. These need to be enabled and configured.
- Security Testing: Used to certify a system; may include testing security management, physical facilities, personnel, procedures, the use of commercial or in-house services (such as networking services), and contingency planning.
- Accreditation: The formal authorization by the accrediting (management) official for system operation and an explicit acceptance of risk.
- Operation/Maintenance: The system is modified by the addition of hardware and software and by other events.
- Security Operations and Administration: Examples include backups, training, managing cryptographic keys, user administration, and patching.
- Operational Assurance: Examines whether a system is operated according to its current security requirements.
- Audits and Monitoring: A system audit is a one-time or periodic event to evaluate security. Monitoring refers to an ongoing activity that examines either the system or the users.
- Disposal: The secure decommission of a system.
- Information: Information may be moved to another system, archived, discarded, or destroyed.
- Media Sanitization: There are three general methods of purging media: overwriting, degaussing (for magnetic media only), and destruction [18].
Notice that the word "secure" or "security" appears somewhere in every step of NIST’s SDLC, from project initiation to disposal: this is the crux of the SDLC.
Note: Security is part of every step of "secure" SDLC on the exam. Any step that omits security is the "wrong answer." Also, any SDLC plan that omits secure disposal as the final lifecycle step is also the "wrong answer."
Many organizations have broadened the SDLC process, beginning with the framework described in NIST SP 800-14 and adding more steps. The United States Department of Justice (DOJ) describes a 10-step SDLC (see here). The text from the DOJ SDLC graphic, shown in Fig. 9.7, is summarized here:
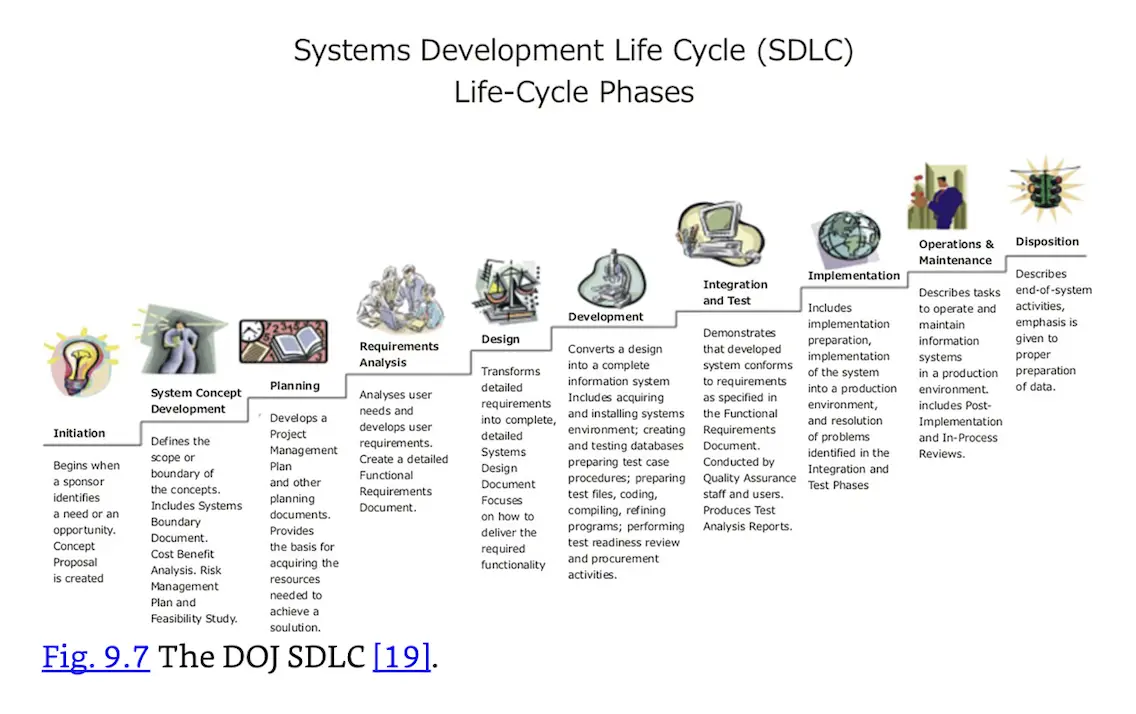 Fig. 9.7 The DOJ SDLC
Fig. 9.7 The DOJ SDLC