Page410
- EMI issues such as crosstalk primarily impact which aspect of security?
A. Confidentiality
B. Integrity
C. Availability
D. Authentication
Correct Answer and Explanation: B. Answer B is correct; while EMI issues such as crosstalk could impact all aspects listed, it most commonly impacts integrity.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect; confidentiality can be impacted (such as hearing another conversation on a voice phone call), and in extreme cases availability and authentication could be impacted (where crosstalk is so severe as to stop systems from functioning). These scenarios are far less common than simple integrity violation caused by EMI issues such as crosstalk.
- What is the most important goal of fire suppression systems?
A. Preservation of critical data
B. Safety of personnel
C. Building integrity
D. Quickly extinguishing a fire
Correct Answer and Explanation: B. Answer B is correct; personnel safety is the paramount concern of the physical (environmental) security domain.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect; all are valid concerns, but less important than safety. Data protection is always a secondary concern to safety; this is why water is the recommended fire extinguishing agent. Building integrity and quickly extinguishing the fire are also important and impact safety, but safety itself is the goal, and thus a stronger answer. The integrity of an empty building is a lesser concern, for example, and while the speed of extinguishing a fire is important, the safety of personnel who must evacuate is a more important concern. The fastest way to extinguish a fire is to starve it of oxygen, which would be deadly to people.
- Which of the following statements regarding containers and virtual machines is true?
A. Both containers and virtual machines share the same kernel
B. Virtual machines share the same kernel; containers use their own kernel
C. Containers share the same kernel; virtual machines use their own kernel
D. Both containers and virtual machines use their own kernel
Correct Answer and Explanation: C. Answer C is correct; containers share the same kernel, virtual machines use their own kernel.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect.
- Non-repudiation is best described as what?
A. Proving a user performed a transaction
B. Proving a transaction did not change
C. Authenticating a transaction
D. Proving a user performed a transaction that did not change
Correct Answer and Explanation: D. Answer D is correct; non-repudiation is proof that a user performed a transaction and proof that it did not change.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Proving a transaction did not change is one half of non-repudiation; proving a transaction did not change is the other half. Non-repudiation requires both. Authenticating a transaction is another way of saying a user performed the transaction and is also one half of non-repudiation.
- Hotspot: you receive the following signed email from Roy Batty. You determine that the email is not authentic, or has changed since it was sent. Click on the locally generated message digest that proves the email lacks non-repudiation (Fig. A.3).
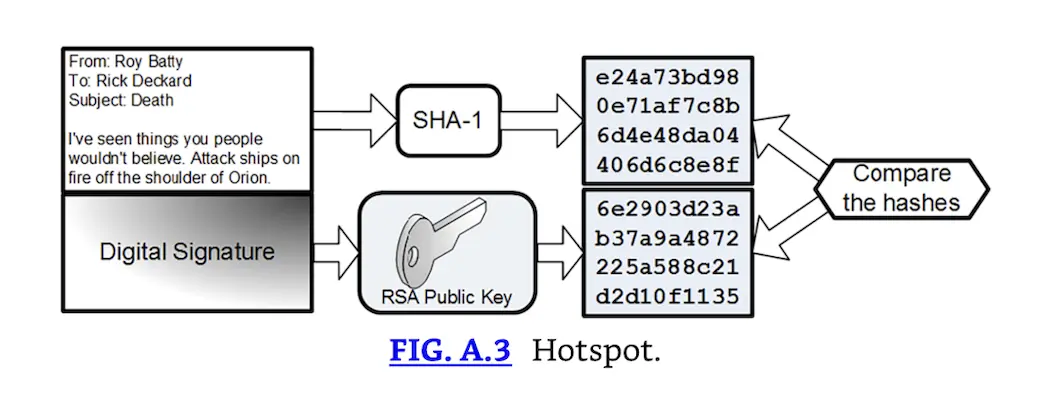 Hotspot.
Hotspot.
Correct Answer and Explanation: The output of a hash algorithm such as SHA-1 is called a message digest. The message digest on the top right of the diagram below is the locally generated hash that does not match the original hash received by decrypting the digital signature with the creator's public key (Fig. A.4).
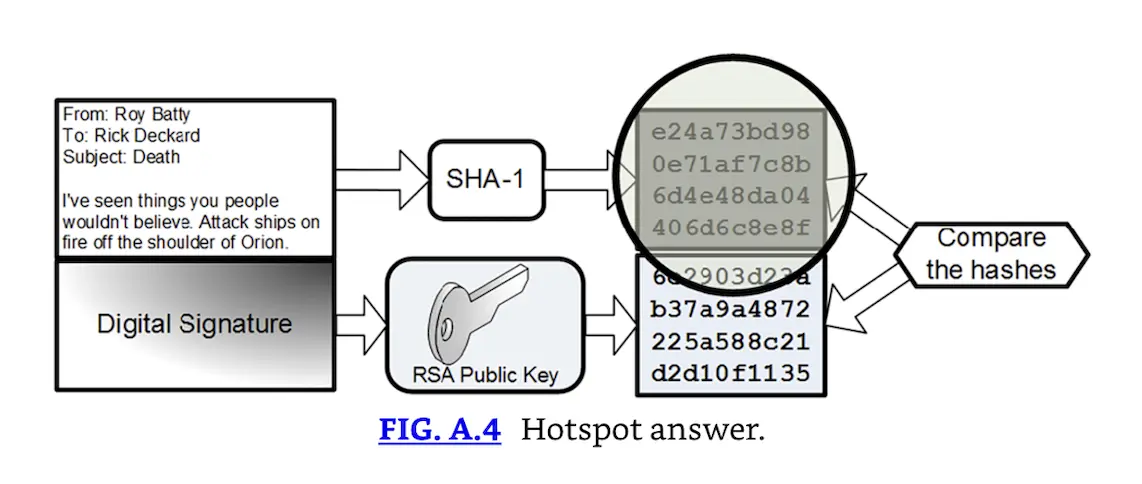 Hotspot answer.
Hotspot answer.
Incorrect Answers and Explanations: The other clickable areas of the hotspot are not locally generated hashes that proves the email lacks non-repudiation.