Page421
- Assuming the penetration test is successful, what is the best way for the penetration testing firm to demonstrate the risk of theft of financial data?
A. Instruct the penetration testing team to conduct a thorough vulnerability assessment of the server containing financial data
B. Instruct the penetration testing team to download financial data, redact it, and report accordingly
C. Instruct the penetration testing team that they may only download financial data via an encrypted and authenticated channel
D. Place a harmless "flag" file in the same location as the financial data, and inform the penetration testing team to download the flag
Correct Answer and Explanation: D. Answer D is correct; a flag is a dummy file containing no regulated or sensitive data, placed in the same area of the system as the credit card data, and protected with the same permissions. If the tester can read and/or write to that file, then they prove they could have done the same to the credit card data.
Incorrect Answers and Explanations: A, B, and C. Answers A, B, and C are incorrect. Answer A is a vulnerability assessment, not a penetration test. Answers B and C are dangerous and could involve unauthorized access of regulated data, such as healthcare records.
- What type of penetration test will result in the most efficient use of time and hourly consultant expenses?
A. Automated knowledge
B. Full knowledge
C. Partial knowledge
D. Zero knowledge
Correct Answer and Explanation: B. Answer B is correct; a full knowledge test is far more efficient than other forms of penetration tests, allowing the penetration tester to find weaker areas more quickly.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. Automated knowledge is not a valid exam term. Both zero and partial knowledge tests will be less efficient than full knowledge.
- You would like to have the security firm test the new web application, but have decided not to share the underlying source code. What type of test could be used to help determine the security of the custom web application?
A. Secure compiler warnings
B. Fuzzing
C. Static testing
D. White box testing
Correct Answer and Explanation: B. Answer B is correct; Fuzzing is a black box testing method that does not require access to source code.
Incorrect Answers and Explanations: A, C, and D. Answers A, C, and D are incorrect. All are static methods that require access to source code.
- During the course of the penetration test, the testers discover signs of an active compromise of the new custom-developed three-tier web application. What is their best source of action?
A. Attempt to contain and eradicate the malicious activity
B. Continue the test
C. Quietly end the test, immediately call the operational IT contact, and escalate the issue
D. Shut the server down
Correct Answer and Explanation: C. Answer C is correct; attackers will often become more malicious if they believe they have been discovered, sometimes violating data and system integrity. The integrity of the system is at risk in this case, and the penetration tester should end the penetration test, and immediately escalate the issue.
Incorrect Answers and Explanations: A, B, and D. Answers A, B, and D are incorrect. The client must be notified immediately, and incident handling is not the penetration tester’s responsibility.
- Drag and drop: Which of the following statements about Syslog are true? Drag and drop all correct answers from left to right FIG. A.5.
 . Drag and drop.
. Drag and drop.
Correct Answer and Explanation: Syslog uses UDP, which offers unreliable transport, so the data is easily spoofed. The data is also not encrypted.
Incorrect Answers and Explanations: Syslog does not use TCP, is not encrypted, and uses no authentication FIG. A.6.
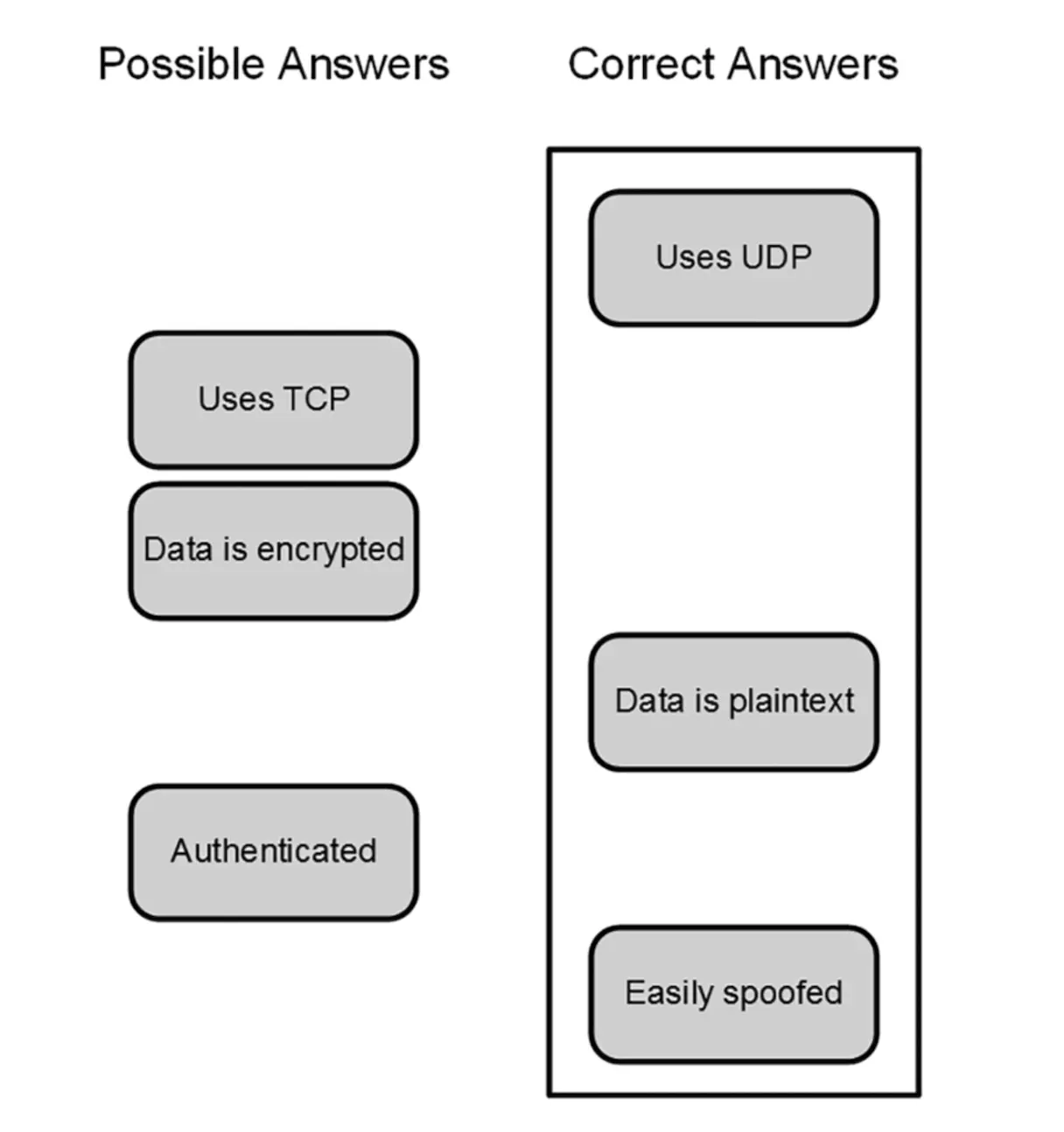 . Drag and drop. - Answer.
. Drag and drop. - Answer.